Effects of Malware and Spam on Business
Malware is indeed a catch-all word for every form of malware, irrespective of how it functions, its purpose, and how it is being transmitted. A virus is a different kind of malware which reproduces itself by incorporating its code into other programs. Computer viruses have indeed been popular since the commercial internet started essentially, whereas, viruses spread via attachment to legitimate files and programs, and thus are circulated through malicious sites, floppy disks, and emails. A user triggers a virus by launching the program or file which is corrupted. A virus can delete or encrypt data, change applications or disable system functions post its enability. There are more than 5 types of malware: virus, worm, trojan horse, spyware and ransomware (McAfee, 2020).
Outbreak Report:
The outbreak report is composed of all those measures that are eventually practiced while carrying out investigation for detecting the outbreak. It is comprised of all the specific time, dates and the types of viruses detected so far in the system.
Zero hour: It is an advanced threat security tool that aims to prevent certain zero-day and advanced threats away from breaking into the infrastructure of an enterprise. Such risks are typically designed to disguise the target organization as major traffic and circumvent security procedures. For such a planned attack, these can be a malicious script, URL or a built mail.
Last outbreak was detected on 29 April 2017.
No ransomwares or trojans were detected.
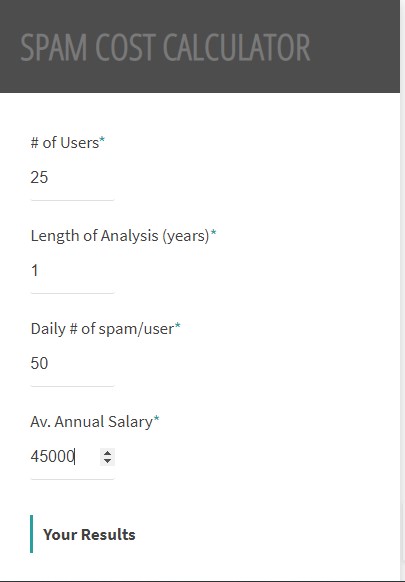
Yearly cost of spam to a company that has 25 employees earning on an average of $45,000 a year and receiving 50 messages per day, of which 75 percent is spam= $ 21, 619.

References
McAfee. (2020). What Is the Difference Between Malware and a Virus? | McAfee. Mcafee.com. Retrieved from https://www.mcafee.com/enterprise/en-us/security-awareness/ransomware/malware-vs-viruses.html.
Information System Management Assessment List


