State of IT Security
{`
Kelly School of Business
Indiana University
Information Systems Graduate Programs
`}
There are two types of companies: those who have been hacked, and those who don’t yet know they have been hacked.
John Chambers, Executive Chairman and former CEO of Cisco
Kelley MBA '76, Academy of Alumni Fellows 1996
Agenda
- Cyber crime statistics
- Information security trends for 2018
- Digital business and information security
- Common threats and vulnerabilities
- Anatomy of attacks and data breaches
- Conclusion
Global cyber crime statistics and costs of cyber crime paint an alarming picture

Source: http://www2.deloitte.com/content/dam/Deloitte/xe/Documents/AboutDeloitte/mepovdocuments/mepov17/are-you-safe-mepov17.pdf
Source: https://www.symantec.com/content/dam/symantec/docs/reports/istr-21-2016en.pdf?aid=elq_&om_sem_kw=elq_16202357&om_ext_cid=biz_email_elq_&elqTrackId=283a3acdb3f f42f4a70ab5a9f236eb71&elqaid=2902&elqat=2
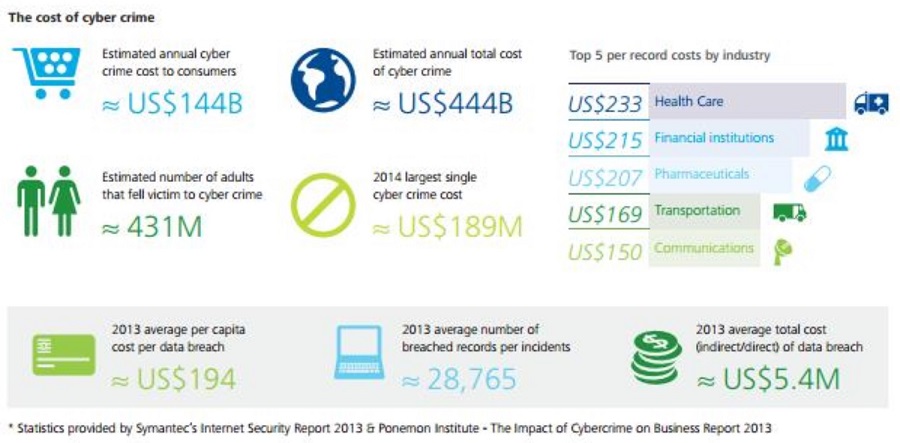
Interesting statistics revealed by Norton’s security survey
70% 431
MILLION U.S. consumers would rather More than 1/3 (36%) of those sharing NEW RANSOMEWARE cancel dinner plans with a best passwords in the U.S. Have shared the VARIANTS friend than have to cancel their password to their banking account +36% in 2015 debit/credit card.
Two in three believe it is riskier to share their email password with their friend than lend them their car.
63% would rather go on a bad date than have to deal with customer service after a security breach.
Source: Norton cybersecurity Insight report - https://us.norton.com/norton-cybersecurity-insights-reportglobal
Gartner's Top Security Trends for 2018
Senior business executives are finally aware that cybersecurity has a significant impact on the ability to achieve business goals and protect corporate reputation
GDPR and data protection regulations impact digital business strategies
Geopolitical security impacts where businesses buy their products from
Security products are rapidly exploiting cloud delivery to provide more agile solutions.
Machine learning is providing value in simple security tasks and elevating suspicious events for human analysis.
Source: “Top Security and Risk Management Trends,” Gartner
Information security and the CIA triad
Information Security – NIST defines Information security as ‘The protection of information and information systems from unauthorized access, use, disclosure, disruption, modification, or destruction in order to provide confidentiality, integrity, and availability’
The objective of information system security is to :
- optimize the performance of an organization with respect to the risks to which it is exposed • preserve goals of information security
Preserving authorized restrictions on information access and disclosure, including means for protecting personal privacy and proprietary information
The property that sensitive data has not been modified or deleted in an unauthorized and undetected manner
Ensuring timely and reliable access to and use of information.
Source: http://nvlpubs.nist.gov/nistpubs/ir/2013/NIST.IR.7298r2.pdf
Gartner’s proposed information security tetrad for digital business
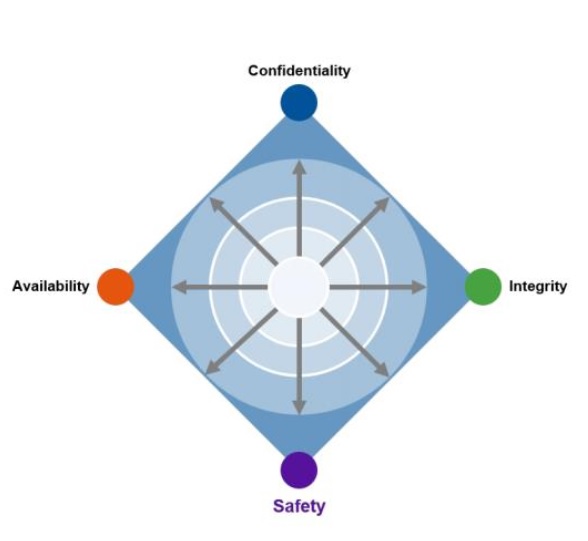
“Protecting information alone isn't enough, and ensuring the confidentiality, integrity and availability of that information isn't enough. Leaders in risk and cybersecurity must now assume the responsibility of providing safety for both people and their environments or, at minimum, participate in providing that safety with other security practices”
Source: “Managing Risk and Security at the Speed of Digital Business “ Gartner
Two key characteristics of digital business are challenging conventional IT control:
- As the business claims increasing autonomy in deploying new digital technologies, it degrades the authority of the central IT organization.
- The dramatic increase in the number of elements (e.g., systems, devices, things, data and dynamic relationships) exposes scalability issues with many traditional security control solutions.
Digital business requires more robust security
- Programs must also allow for new value to be created through disruptive technologies while sensibly managing risks. Security must adapt to a digital business strategy or ironically expose the enterprise to even greater risk
Security must be designed to align with a digital business strategy. Conventional principles must be challenged to support business agility
Define, communicate and enforce security policies with all stakeholders
Continually assess and improve maturity and performance
Sources: “Managing Risk and Security at the Speed of Digital Business,” Gartner
Common security threats and vulnerabilities
Common security threats
Social engineering
Crime ware like Ransomware
- 2.
- Insider vulnerabilities
- Information warfare
- Malicious code
- Mobile code
- Denial of service attacks
- Spam, Phishing and Trojans
- Web based vulnerabilities like SQL injection, cross site scripting
- Physical threats to Information Infrastructure
Source: Computer Security Handbook, Sixth edition
Social engineering remains amongst the top 3 causes for data breaches
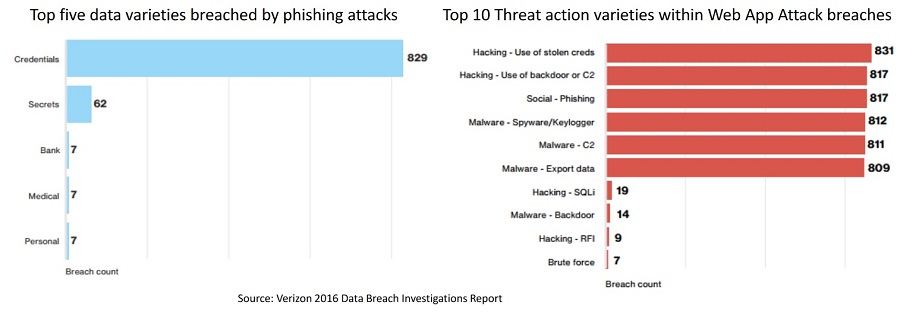
Top five data varieties breached by phishing attacks Top 10 Threat action varieties within Web App Attack breaches
Source: Verizon 2016 Data Breach Investigations Report
Social Engineering Example: Gmail password reset scam
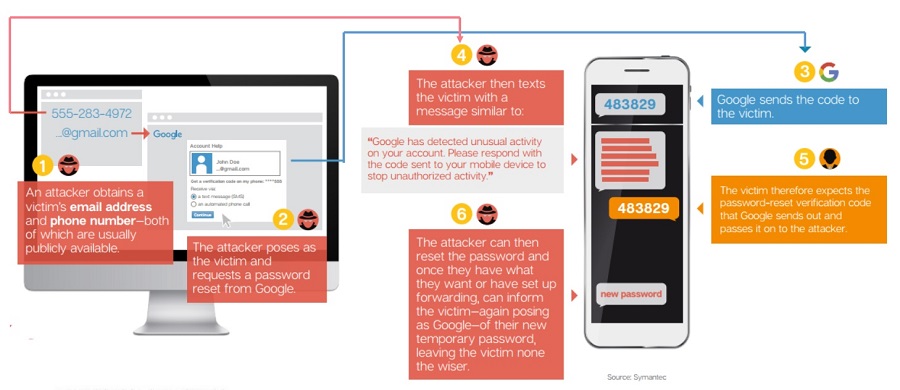
CIO magazine states that 93% of phishing emails are now ransomware
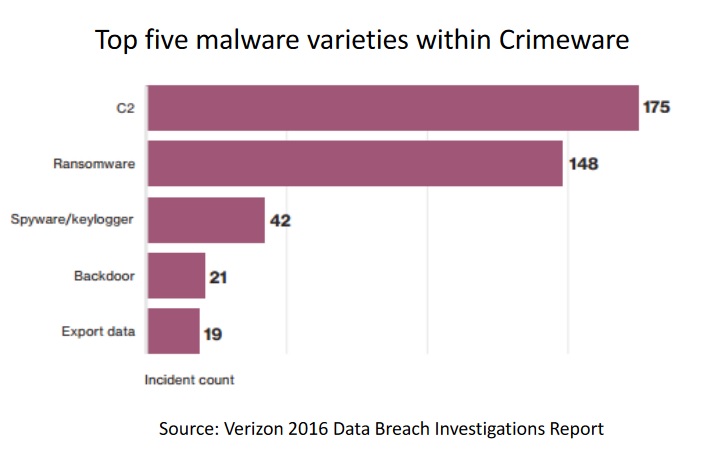
- Ransomware is a type of malware that prevents Top five malware varieties within Crimeware or limits users from accessing their system, either by locking the system's screen or by locking the users' files unless a ransom is paid.
- More modern ransomware families, collectively categorized as crypto-ransomware, encrypt certain file types on infected systems and forces users to pay the ransom through certain online payment methods to get a decrypt key.
Source: Verizon 2016 Data Breach Investigations Report
Source: http://www.trendmicro.com/vinfo/us/security/definition/ransomware
Russian-based hacking organization offering Ransomware-as-a-Service
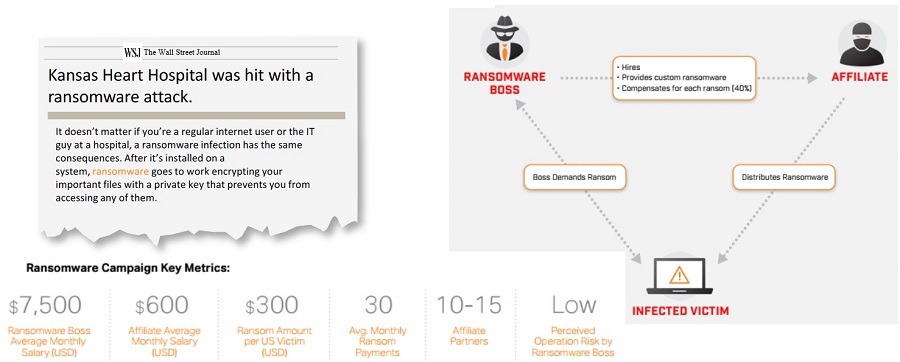
Source: https://www.flashpoint-intel.com/home/assets/Media/Flashpoint_Ransomware_April2016.pdf Source: http://www.extremetech.com/extreme/229162-hospital-pays-ransomware-but-doesnt-get-filesdecrypted
Anatomy of attacks that cause data breaches
Zero day vulnerabilities and ICS vulnerabilities
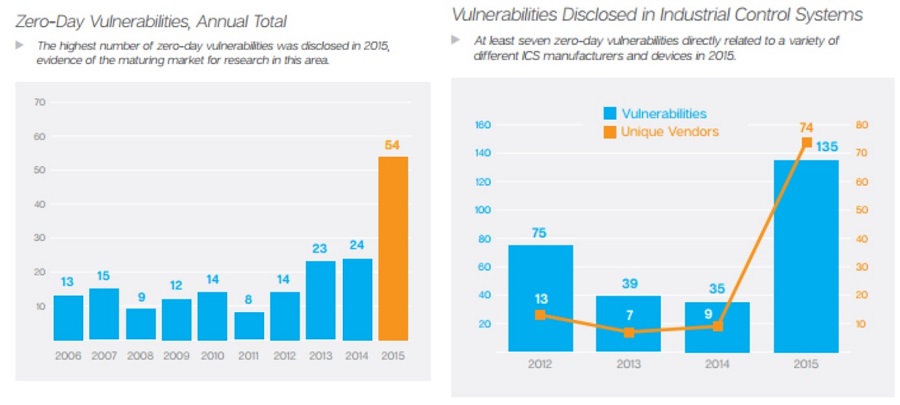
Source: https://www.symantec.com/content/dam/symantec/docs/reports/istr-21-2016-
en.pdf?aid=elq_&om_sem_kw=elq_16202357&om_ext_cid=biz_email_elq_&elqTrackId=283a3acdb3ff 42f4a70ab5a9f236eb71&elqaid=2902&elqat=2
Data breaches in 2017

Source: https://frankonfraud.com/fraud-trends/data-breach-index-is-going-off-a-cliff-in-2017/
The cost of data breaches in 2017
- Verizon received a $350 million discount on their purchase of Yahoo! as a result of Yahoo!'s data breach, which resulted in a failure to hit the standard of due care.
- Maersk took a $300 million expense as a result of a massive ransomware attack.
- Equifax's breach cost the CEO, CIO, and the CSO their jobs, and will have a continuing significant financial impact.
- Global economic losses from the {"WannaCry"} attack was estimated to be between $1.5 and $4 billion.
Source: Verizon 2016 Data Breach Investigations Report
As cybercrime increases at an alarming rate, more collaboration between senior business managers and information security professionals is required
We need a holistic approach to security to reduce organizational risk
http://www.informationisbeautiful.net/visualizations/worlds-biggest-data-breaches-hacks/
How does this impact you?
- The demand for security skills — both classic technical skills as well as businessoriented skills — continues to be greater than the available supply
- Mature security organizations are investing in security and risk managers that have the background and experience
to work closely with business stakeholders to understand their risk appetite and risk tolerance
Sources: “Top Security and Risk Management Trends,” Gartner; “Managing Risk and Security at the Speed of Digital Business,” Gartner
References
- Computer Security Handbook, Sixth Edition
- https://us.norton.com/norton-cybersecurity-insights-report-global
- Symantec security threat report 2015
- Kaspersky statistics for 2015
- Deloitte report on Cyber security 2015
- NIST Glossary of Key Information Security Terms
- http://nvlpubs.nist.gov/nistpubs/ir/2013/NIST.IR.7298r2.pdf
Appendix
Insider threat incident statistics for 2015
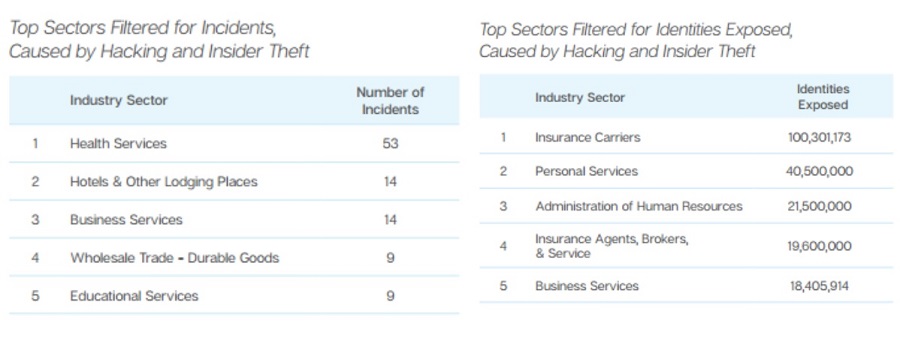
Source: https://www.symantec.com/content/dam/symantec/docs/reports/istr-21-2016-en.pdf?aid=elq_&om_sem_kw=elq_16202357&om_ext_cid=biz_email_elq_&elqTrackId=283a3acdb3ff 42f4a70ab5a9f236eb71&elqaid=2902&elqat=2
Distribution of the benchmark sample by root
cause of the data breach
Source: http://www-01.ibm.com/common/ssi/cgibin/ssialias?subtype=WH&infotype=S A&htmlfid=SEW03053WWEN&attach ment=SEW03053WWEN.PDF
Percentage direct and indirect per capita data breach costs
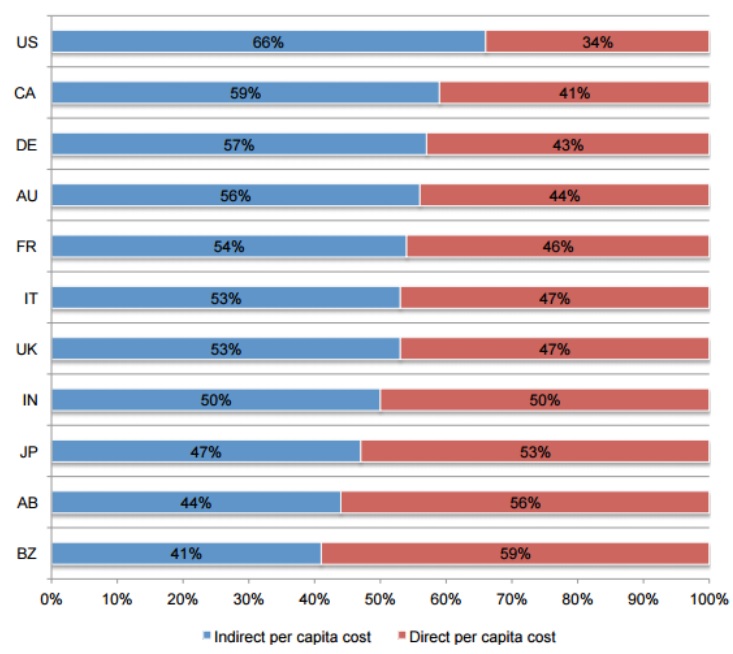
Source: http://www01.ibm.com/common/ssi/cgibin/ssialias?subtype=WH&infotype=S A&htmlfid=SEW03053WWEN&attach ment=SEW03053WWEN.PDF
Vulnerabilities identified for 2015
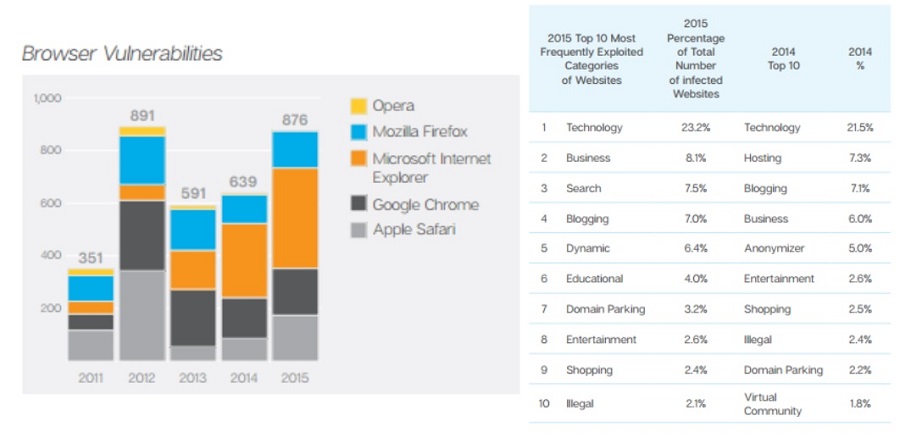
Source: https://www.symantec.com/content/dam/symantec/docs/reports/istr-21-2016en.pdf?aid=elq_&om_sem_kw=elq_16202357&om_ext_cid=biz_email_elq_&elqTrackId=283a3acdb3ff42f4a730 0ab5a9f236eb71&elqaid=2902&elqat=2
Law enforcement is the rising breach discovery method over time
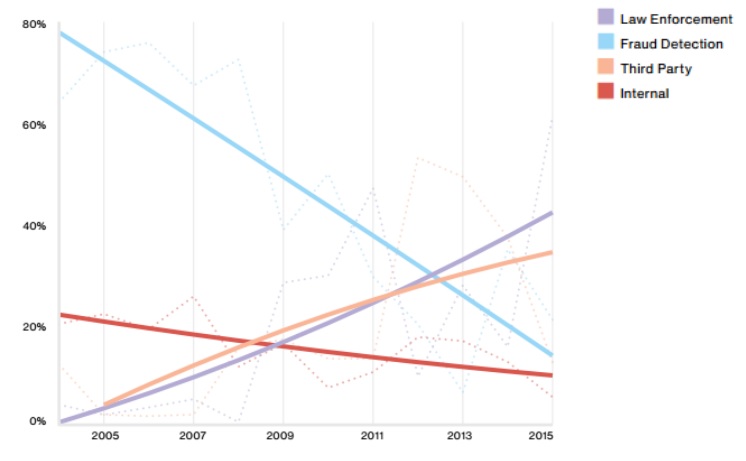
Source: Verizon 2016 Data Breach Investigations Report


