Lab 1 Assignment Evaluating Web Server Vulnerabilities
Lab Screen Shots
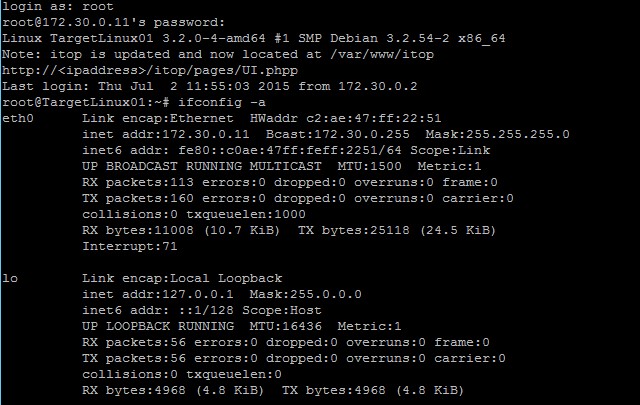
Part 1 Step 6 Screen Shot Make a screen capture showing the IP address
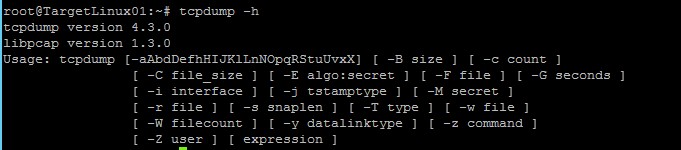
Part 1 Step 9 Screen Shot Make a screen capture showing the IP address
Lab Assessment Questions
|
1. What are some of the greatest risks businesses face when connecting to the Web? Why? Unauthorized access to security information, which can prompt potential claims. Compromise of client security information, which is a consistence law infringement. Compromise of MasterCard information and location check information prompting PCI DSS rebelliousness and potential claims. Lawsuits from client or business accomplices coming about because of loss of classified data, which, thusly, can bring about a loss of income and business belie. |
|
2. Why is it critical to perform periodic Web-application vulnerability assessments and penetration tests? It is critical because when you apply some operation like update, install or upgrade version software or web application in server. Before that we need to check the environment and the server. A full vulnerability-assessment check and than penetration tests should be performed for maintaining compliance and ensure confidentiality, integrity, and availability (CIA) for the Web server and the Web application. |
|
3. Why might connecting your Web servers and Web applications to the Internet be like opening Pandora’s box? Connecting with web server and application to the internet be like opening Pandora’s box because by connecting with the web, you are opening your data up to programmers that can unite through the web. |
|
4. What does the Skipfish application do, and why is it a good security tool for Web servers and Web-application testing? Skipfish is a mechanized web application vulnerability scanner accessible for nothing download at Google's code site. It is a scanner security experts can use to assess the security profile they could call their own locales. It slithers the site and after that check every pages for different security dangers and toward the end readies the last report. It is exceedingly streamlined for HTTP taking care of and using least CPU. It guarantees that it can undoubtedly handle 2000 solicitations for every second without including a heap CPU. It utilizes a heuristics methodology while slithering and testing site pages. This device additionally claims to offer brilliant and less false positives. This apparatus is accessible for Linux, FreeBSD, MacOS X and Windows. Because of above result Skipfish is good security tool. |
|
5. What is tcpdump, and why is it a good tool for testing the Ubuntu Linux Web server and Web-application security? tcpdump is a typical bundle analyzer that keeps running under the summon line. It permits the client to show TCP/IP and different bundles being transmitted or got more than a system to which the PC is appended. It is good tool because it gives permit to see activity convention testing and it is a convention catch and analyzer instrument that empowers Ubuntu Linux server to catch server communication. |
|
6. What does the Firefox Live HTTP Headers plug-in application do, and why is this a good tool for Web-server and Web-application security testing? The Firefox Live HTTP Headers is a truly accommodating infiltration testing extra for Firefox. It shows live headers of each http solicitation and reaction. You can likewise spare header data by tapping on the catch in the lower left corner. I don't feel that there is any sort of need to tell how critical this extra is for the security testing procedure. So that it is good tool for Web-server and Web-application security testing. |
|
7. What does using the -h switch for tcpdump and skipfish do? Using the -h switch is the help information for tcpdump and Skipfish. |
|
8. What is the tcpdump usage message that you recorded during this lab? |
|
9. What information can you determine from the ifconfig -a command? By using ifconfig –a command, we determine Information of all active or inactive network interfaces on server including Ethernet (eth0) and local loopback (lo). |


