Information Technology in Organizational Functions
Chapter 1: Introduction
Introduction
The organizational functions in the current era have undergone immense changes, and ways of conducting their operational activities for product and service delivery has also changed a lot. The changes that the organizations have experienced are tremendous technological changes. The IT sector after the advent and in the current phase of globalisation has made significant advancement and at the same time the organisations in the present era of globalisation has opted for incorporating the aspects of information technology (IT) within its core organisational functions and activities. Organisations by incorporating IT as an integral part of organisations overall function aims to achieve its desired goals and objectives. Therefore, the following research study evaluates the role of IT in achieving organisational goals and objectives and the ways for effectively applying the same in the operations and other functions of an organisation.
Background of the study
It is quiet evident that IT plays a crucial role in each and every aspect of an organization. With the application of IT the product and service delivery along with other organizational task are being performed more efficiently in comparison to traditional methods and further with the incorporation of IT organizations can avail fertile ground for implementing innovation in the various organizational functions and activities. Moreover, the current business enterprises or organizations are highly concerned with the issues of data protection and security and therefore in order to keep data and information intact the current organizations opt for the usage of IT security protocols.
Research aim
Considering the extensive use of information technology (IT) by organization in the current era the following research study aims to determine the role of IT in allowing organization for enhancing its productivity and growth and the role of IT in protecting volumes of data and information in an efficient manner.
Research objectives
The major objectives of the given research study are as follows:
- To determine process and procedure of implementing effective IT resources for organizational goals and development
- To determine role of IT in cyber security
- Recommend best possible measures of efficient and effective utilization of and incorporation IT in organizational functions and activities
Research questions
Question for the given research study is as follows:
- What is the relation between IT and organizational functions?
- How can IT help in maintaining cybersecurity?
Chapter 2: Literature Review
The research study in the literature review section will evaluate the theoretical framework of various research studies relative to undertaken subject matter. The aim of conducting the following literature review is obtain a detail insight on the research topic by scrutinizing relevant studies on the chosen topic and further comprehend the proper measures for implementing information technology in organizational context and accordingly determine its effectiveness in fostering organizational growth and sustainability.
The role of IT for organizational growth implies the ways an organization can develop its self by adapting to changes and incorporating productive resources for its sustainability. (AllenRodgera & A.Georgeb1, 2017), states that in order to ensure organizational development the management needs to identify the relevant resources that increase its productivity. This implies that in the case of implementing IT within the organizational activities the management is required to first identify it need and then determine the suitable IT resource that assist the organization in improving its regular functions. However, (Day & Schoemaker, 2016) suggest that apart from accessing needs organization also needs to emphasize on the changes that occurs in the contemporary functions such as following the latest trends in the usage of IT in order to sustain along with the competitors in a specific industry.
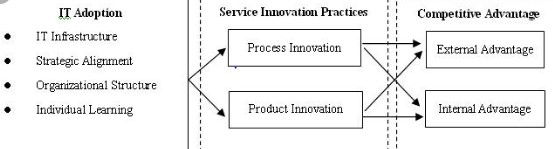
Figure 1: Strategic implementation of IT within organizational activities
(Source: Day & Schoemaker, 2016)
(Eyad Sameh Alkronz, 2019), in the context of implementing and incorporating information technology for organizational advancement states that since the current organizational practices are driven on the basis of data, therefore the inclusion of technology that is easy to use and handle, and that provides comprehensive data for the stakeholders as well as the technology should to operate for conducting the daily operations of an organization. On the other hand (Safaa, Solmsa, & StevenFurnellab, 2016), argues that even though the information technology has improved with time there is a lack of an effective integrated process that can assist the overall function of an organization. Thus, the given statement signifies that since the current organization mostly are data driven and primarily operates by relying on certain information, therefore a system for processing various information at a time and keeping such information secure at its highest level is essential for organization in the current era.
In continuation to the above disAssignment it very well may be said that for the executives of data and information, associations are required figure powerful approaches and in such manner information security is of most noteworthy concern. (Soomro, HussainShah, and JavedAhmed, 2016), makes reference to that with the rise of distributed computing the dangers to information security and wellbeing has expanded, and a few research studies recommend that the association working in the momentum market will in general depend on distributed computing. In such situation the inquiry that emerges is the thing that measures can be embraced for verifying the information and keeping up its trustworthiness. In addition to this, further research studies have suggested that the organizations in the near future are likely use cloud computing, which as per (T.Pereiraab, L.Barretoac, & A.Amaralab, 2017), can lead the increase in expenses for organization being the cost that will be incurred is on the cost of security.
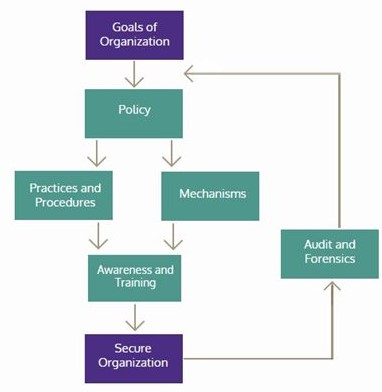
Figure 2: proposed steps for implementing cyber security procedure in an organization
(Source: Eyad Sameh Alkronz, 2019)
Chapter 3: Methodology
The following research will be conducted by analysing the organizational structure and thereby determine the needs for change or implementing IT in the respective organization. The research study will also determine the changes in business practices undertaken by the organization and identify the measures existing for developing internal productivity and growth. Further, the decision making process will be evaluated along with the measures under taken for processing regular operations. Moreover, the organizations approach in service delivery along with the measures undertaken for innovation will be identified. Accordingly, the process involving the management of internal and external stakeholders will be examined in the research study and at the same time competitor analysis will be conducted in order to assume the measures undertaken by different participant within the same industry. Further, with respect to competitors the research study will analyse the measures for implementing new service strategy for enhancing its competitive advantage along with the ways to provide better customer services.
Chapter 4: Data analysis
The data for the given research study will be analysed based on the qualitative data. For the given research study qualitative data is considered as it can allows to gather detailed overview on the chosen subject matter. Moreover, since such data are based on existing information therefore it can allow in obtaining relevant information regarding the subject matter. Subsequently, it can also be stated that in the case of qualitative data the information mostly results from observations and actual experience therefore it can allow to present the information in a precise manner. Lastly, qualitative data further allows predicting the future possibilities of occurrence based on the current data and information.
Chapter 5: Conclusion
Research limitations
The limitation in association with the given research study that can be assumed is lack of sufficient timeframe for collecting the ample amount of data. On the other hand, another limitation with the research study that might arise is availability of sufficient funds for the research study. Apart from that the lack of cooperation from the team members can create constraints in completion of the research. Moreover, in case of inadequate funds the sample size of the research can get affected, which might further impact the amount of data and information concentrated in the research study.
- Synthesis Matrix
|
Main Idea A |
Main Idea B |
Main Idea C | |
|
Article#1: Triple bottom line accounting for optimising natural gas sustainability: A measurable direct programming fluffy ILOWA improved sustainment model way to deal with diminishing production network worldwide digital security defenselessness through data and communications technology. |
Sustainable economy model that maintain the constructive elements of private capitalism and bookkeeping standards while improving coordinated effort between industry, landowners, and earthy people to streamline return on benefits for organizations, give values to landowners, and fulfill the planets' ecological concerns.. |
Need to preserve the best qualities of free enterprise and market-driven regulation profits while also providing social and environmental benefits. |
Sustainability, risk management and Data and communication technology |
|
Article#2: The Organizational Structure and its Role in Applying the Information Technology Used In the Palestinian Universities |
Organizational Structure and its role in applying the Information Technology |
Information Technology Used from way of authoritative staff, there is an immediate connection between's The Organizational Structure and the Information Technology Used, the job and effect of The Organizational Structure in the idea of the Information Technology Used |
the necessity for universities to proceed with paying attention to the gradual improvement of the Information Technology Used and to give strength to the democratic leadership style and empowering university staff |
|
Article#3: Adapting to Fast-Changing Markets and Technologies |
long-term biofuel investment by DuPont and Novartis's rapid deployment of digital technologies in marketing |
Technological changes, market analysis |
Crowdsourcing, Databases, Business-Government Relations |
|
Article#4: Information security policy compliance model in organizations |
Information security policy compliance protects information assets in organizations |
Association decidedly impacts data security arrangement consistence |
Commitment positively influences information security policy compliance. |
|
Article#5: Human aspects of information security in organisations |
technological aspects play a core integrative role in information security |
technological and organisational control aspects are critically important |
Information security technology cannot guarantee the safety of information assets in organisations |
Reference List
AllenRodgera, J., & A.Georgeb1, J. (2017). Triple bottom line accounting for optimizing natural gas sustainability: A statistical linear programming fuzzy ILOWA optimized sustainment model approach to reducing supply chain global cybersecurity vulnerability through information and communications t. Journal of Cleaner Production.
Day, G. S., & Schoemaker, P. J. (2016). Adapting to Fast-Changing Markets and Technologies. Adapting to Fast-Changing Markets and Technologies.
Eyad Sameh Alkronz, K. A.-N.-N. (2019). The Organizational Structure and its Role in Applying the Information Technology Used In the Palestinian Universities- Comparative Assignment between Al-Azhar and the Islamic Universities. International journal of academic and applied research.
Safaa, p., Solmsa, R., & StevenFurnellab. (2016). Information security policy compliance model in organizations. Computers & Security.
Soomro, Z. A., HussainShah, M., & JavedAhmed. (2016). Information security management needs more holistic approach: A literature review. International Journal of Information Management.
T.Pereiraab, L.Barretoac, & A.Amaralab. (2017). Network and information security challenges within Industry 4.0 paradigm. Procedia Manufacturing.


