Identity and Access Management Part 2
{`
Kelly School of Business
Indiana University
Information Systems Graduate Programs
`}
Part 2: Identification, Authentication and Authorization + IAM systems
Identity Management
Identification
- Identification is providing the assurance that the entity requesting access is accurately associated with the role defined within the system
- Downstream controls depend on this
- Essential security practices
- Uniqueness
- Each person or entity must be uniquely identified
- Non descriptiveness
- User ID should not expose role or job function (e.g. root, admin, web-admin, hr, finance etc.)
- Secure issuance
- Must use a secure and documented process to issue IDs
Identity Management Implementation
- Implementation of processes and technologies to consolidate and streamline the management of user IDs, authentication, and access information consistently
- Password management
- Account management
- Profile management
- Directory management
- Single sign-on/federated ID management
Password Management
- Centralized password management and synchronization
- Self-registration process
- Set password and reset
- Password policy
- Require users to sign a non-disclosure agreement
- Allow temporary passwords to be used only once
- Never store passwords in clear text
- History of passwords should be maintained so they cannot be reused
- Implement a password lockout mechanism, etc.
Account Management
- Involves creation, modification, and decommissioning of user accounts
- Very complex due to the heterogeneous account management capabilities of various systems and applications, and the difficulty in interfacing
- Essential features
- Central facility for managing user accounts to multiple systems simultaneously
- Workflow system to submit requests for new, changed, or terminated system access
- Automatic replication of user records between multiple directories
Profile Management
- Profile is a collection of information associated with a particular identity or group. Eg. User ID, date of birth, home address, telephone number
- A profile can also contain information related to privileges and rights on specific systems
- Profile management manages and propagates any changes to a user profile to key systems like corporate directory and the individual systems a user logs into
Directory Management
- A corporate directory contains a hierarchy of objects storing information about users, groups, systems, servers, printers, etc.
- Provides a centralized collection of data that can be used by many applications
- Common directory standards
- 500
- Lightweight Directory Access Protocol (LDAP)
- Active Directory Domain Services (ADS/ADDS)
Authentication
Definition
- Authentication is the process of verifying the identity of an user
- The combination of the identity and information only known by the user acts to verify that the user identity is being used by the expected and assigned entity
Factors used for Authentication
- Authentication by knowledge
- “what you know”
- Authentication by ownership
- “what you have”
- Authentication by characteristic
- “what you are”
What a Person Knows
- Most common (user id/pwd)
- Passwords are now considered a vulnerability
- Passwords vs. passphrase
- Confidentiality is critical
- Passwords are stored in a hashed format
- A hash function produces a fixed length representation of any amount of data
- Hash functions are one-way
- So password crackers hash different passwords till a match with the hash is found
Administrator:500:CC5E9ACBAD1B25C9AAD3B435B51404EE:996E6760CDDD8815A2C24A110CF040FB:::
What a Person Has
- Uses a token or physical device
- Can be synchronous or asynchronous
Tokens
- Tokens are used by claimants to prove their identity and authenticate to a system
- Tokens can contain either asymmetric keys or symmetric keys
- Can be software or hardware based
- Software token
- Stored on a device (desktop, laptop, mobile etc.) and require activation trough a second factor or authentication
- Hard token
- Physical tokens that store credentials
- Smart cards, one-time password device
Asynchronous Token System
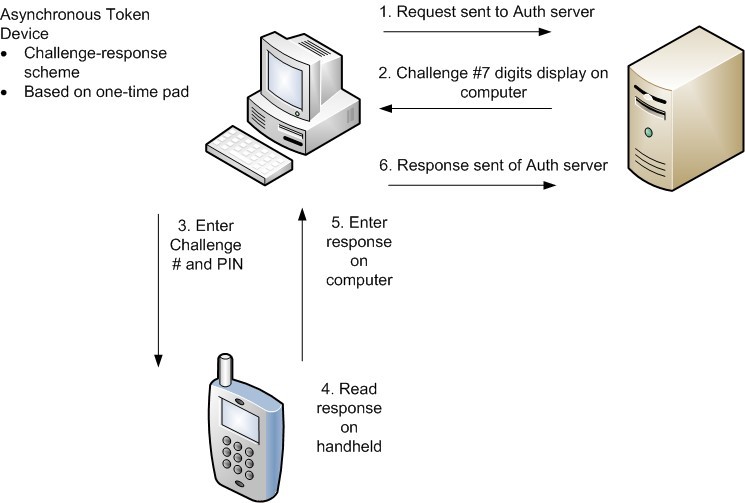
- Based on challengeresponse scheme
- The authentication server will provide a challenge to the remote entity
- Only the token that is assigned to the individual can provide the correct response, which the user will enter to authenticate
Synchronous Token System
- Based on event, location or time-based synchronization
- Time-based model
- User is given a token or smart device that uses an embedded key to generate a unique number or character string in a given timeframe
- User must provide currently displayed number or character string when challenged by the system
What a Person Is
- Biometric authentication
- Physiological
- Fingerprint, facial image, retinal scanning
- Behavioral
- Keystroke dynamics, signature dynamics
- Biometric systems use a technical and mathematical guess to identify a person
- Concerns
- Changing physical and environmental conditions are an issue
- False rejection and false acceptance issues
Biometric Error Rates
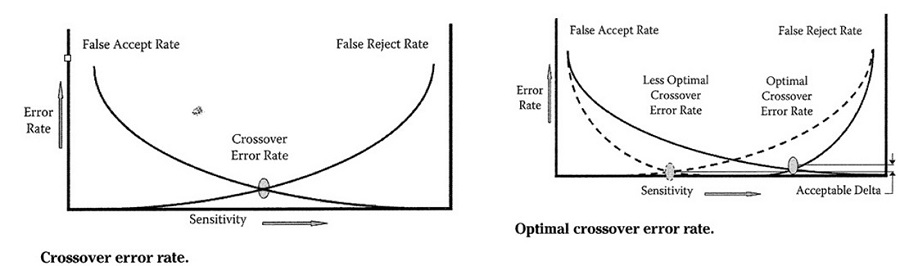
Biometric Considerations
- Resistance to counterfeiting
- Data storage requirements
- User acceptance
- Reliability and accuracy
- g. RBAC with Biometric access
Comparison of Mechanisms
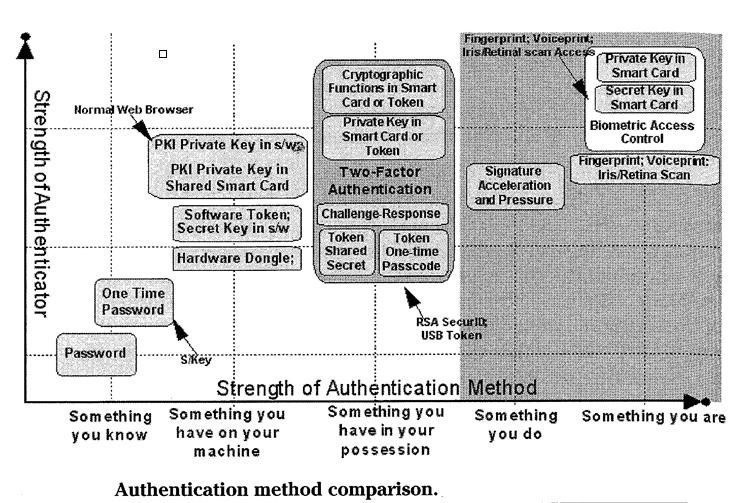
Types of Authentication
- Single factor authentication
- Two factor authentication
- Three factor authentication
Cost Considerations
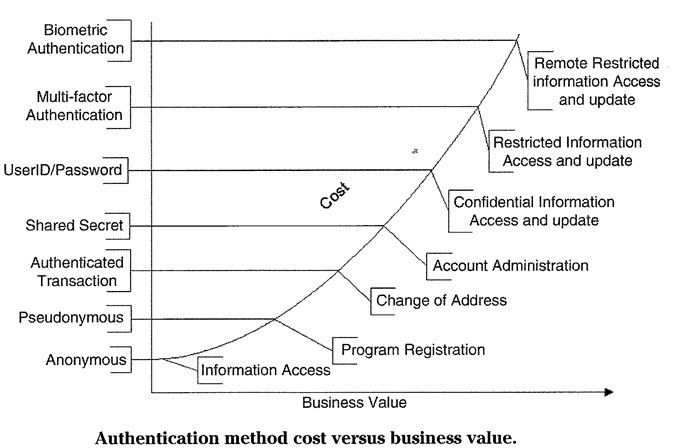
Cost vs. Risk
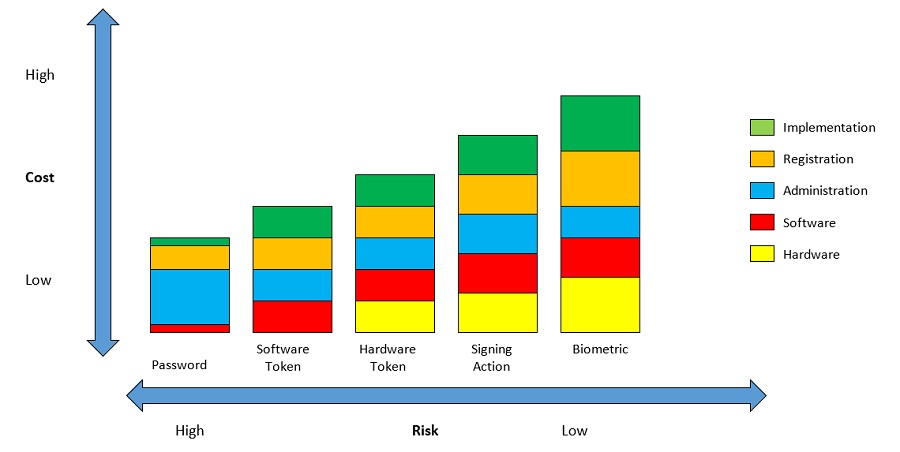
High Risk Low
Authorization
Authorization Mechanisms
- Discretionary Access Controls (DACs)
- Mandatory Access Controls (MACs)
- Access Control Lists (ACLs)
- Roles-Based Access Controls (RBACs)
- Rule-Based Access Controls
- Attribute-Based Access Controls (ABACs)
Discretionary Access Control (DAC)
- Controls placed on data by the owner of the data
- Controls on use are determined by the owner or are at the discretion of the owner
Mandatory Access Control (MAC)
- Controls placed on the data by the owner and the system
- The system will enforce security policies
- Security controls can be based on classification/security clearance of the object
- Only those who are cleared AND have a need to know have access
- System controls the access, and the owner provides the need-to-know control
Access Control List/Matrix
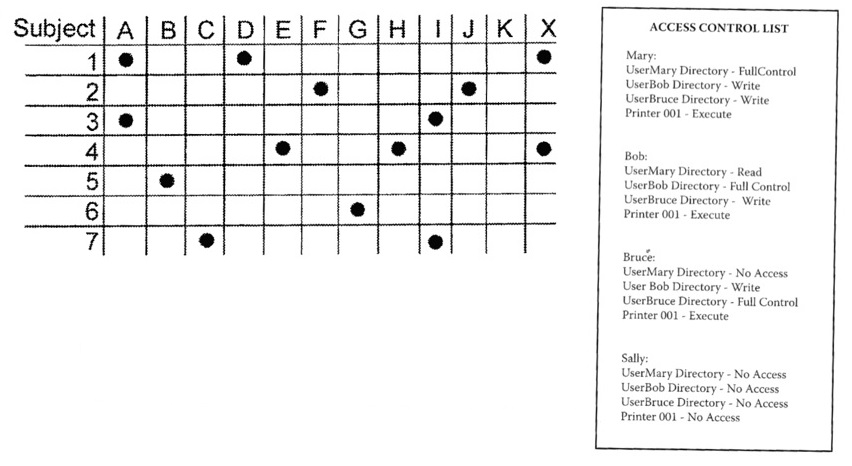
- ACLs are used in the provisioning of permissions within a given system based on policy
- ACM is a set of ACLs in a Matrix
Access Control List/Matrix
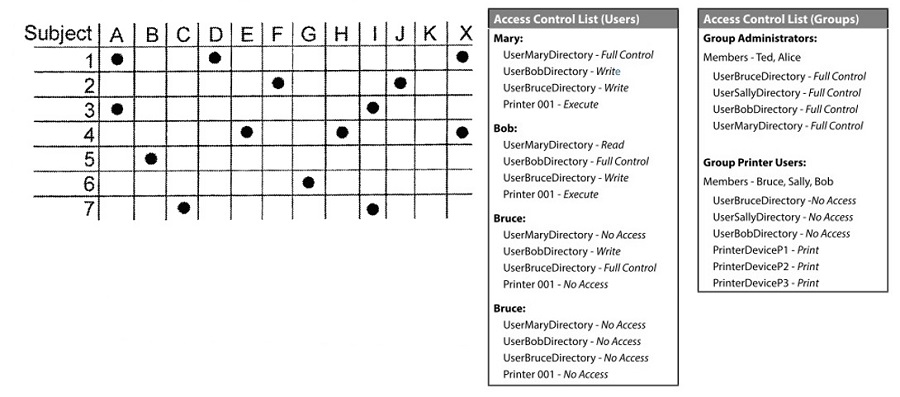
- ACLs are used in the provisioning of permissions within a given system based on policy
- ACM is a set of ACLs in a Matrix
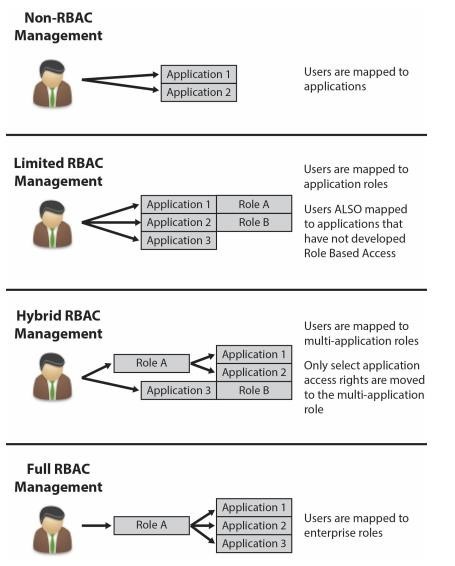
Role-Based Access Control
- Access control is based on the roles (or functions) an user is assigned within an organization
- The determination of roles is done by owner of the data or can be applied based on security policy
- This is also a form of DAC since access is determined by owners of the data/system
- Easy to model
Approaches to RBAC
Rule-Based Access Control
- In a Rule Based Access Control system, access is based on a set of predefined rules which determine what access should be granted
- Rules are created/authorized by system owners
- A form of DAC since users are granted specific privileges by the owner
Attribute Based Access Control (ABAC)
- A logical access control methodology where authorization to perform a set of operations is determined by evaluating attributes associated with the subject, object, requested operations, and, in some cases, environment conditions against policy, rules, or relationships that describe the allowable operations for a given set of attributes.
- Attributes are characteristics that define specific aspects of the subject, object, environment conditions, and/or requested actions that are predefined and pre-assigned by an authority.
- Environmental conditions are dynamic factors, independent of subject and object, that may be used as attributes at decision time to influence an access decision. Examples of environment attributes include time, location, threat level, temperature, etc.
Source: NIST Special Publication 800-162
Basic ABAC Concept
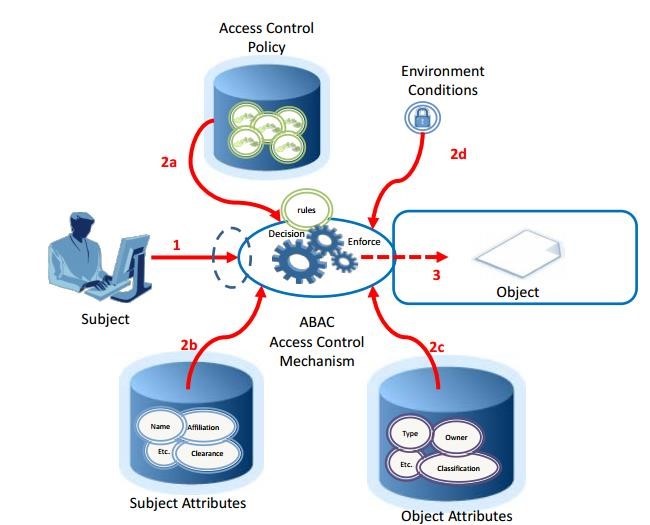
What happens if we scale this up to an Enterprise?
- Subject requests access to object
- Access Control Mechanism evaluates
- Rules
- Subject Attributes
- Object Attributes
- Environment Conditions to compute a decision
- Subject is given access to object if authorized
Source: NIST SP 800-162
… this gets complex
Enterprise ABAC Operations
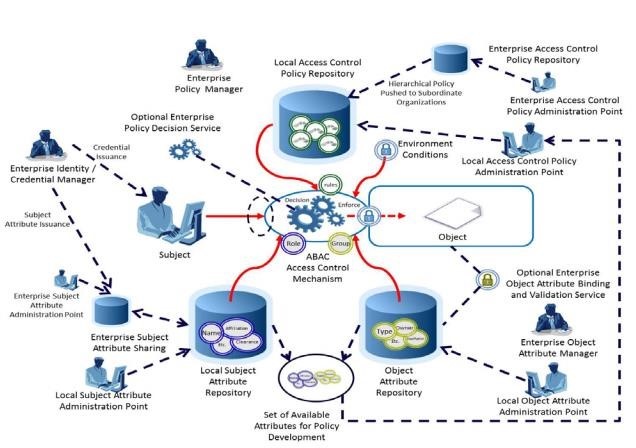
Source: NIST SP 800-162
Combining RBAC and ABAC
- RBAC trades up-front role structuring effort for ease of administration and user permission review, while ABAC makes the reverse trade-off: it is easy to set up, but analyzing or changing user permissions can be problematic.
- ABAC makes it easy to specify access rules, but to determine the permissions available to a particular user a potentially large set of rules might need to be executed in exactly the same order in which the system applies them.
Source:
- “Adding Attributes to Role-Based Access Control”, D. Richard Kuhn, Edward J. Coyne, Timothy R. Weil IEEE Computer, vol. 43, no. 6 (June, 2010) , pp. 79-81
- NIST SP 800-162
Source: “Adding Attributes to Role-Based Access Control”, D. Richard Kuhn, Edward J.
Coyne, Timothy R. Weil IEEE Computer, vol. 43, no. 6 (June, 2010) , pp. 79-81
RBAC-A
- RBAC-A handles the relationship between roles and attributes, while retaining some of the administrative and user permission review advantages of RBAC while allowing the access control system to work in a rapidly changing environment:
- Dynamic roles. Attributes such as time of day are used by a front-end module to determine the subject’s role, retaining a conventional role structure but changing role sets dynamically. Some implementations of dynamic roles might let the user’s role be fully determined by the front-end attribute engine, while others might use the front end only to select from among a predetermined set of authorized roles.
- Attribute-centric. A role name is just one of many attributes. In contrast with conventional RBAC, the role is not a collection of permissions but the name of an attribute called role. This approach’s main drawback is the rapid loss of RBAC’s administrative simplicity as more attributes are added.
- Role-centric. Attributes are added to constrain RBAC. Constraint rules that incorporate attributes can only reduce permissions available to the user, not expand them. Some of ABAC’s flexibility is lost because permission sets are still constrained by role, but the system retains the RBAC capability to determine the maximum set of user-obtainable permissions.
Evolution of Access Control
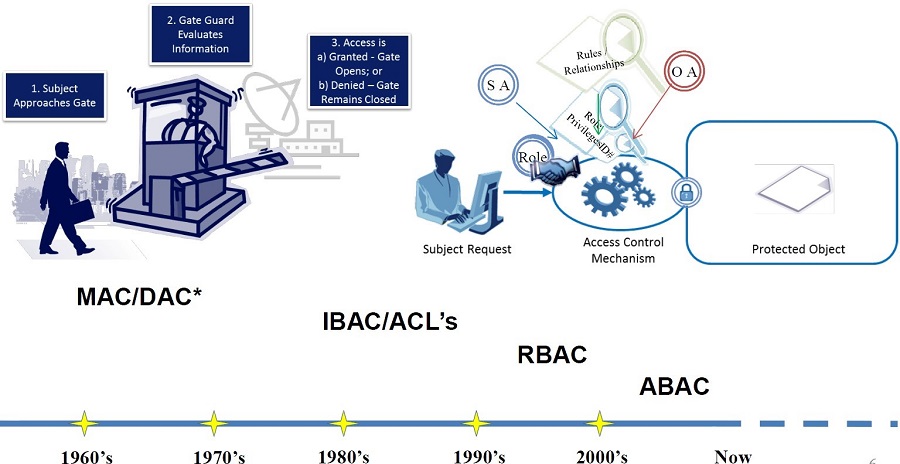
Source: NIST Special Publication 800-162
Access Control Protocols
- Single Sign-on (SSO)
- Kerberos
- Secure European System for Applications in a Multi-Vendor Environment
- Security Assertion Markup Language (SAML)
Single Sign-on (SSO)
- SSO employs a central authorization server to enable a user to authenticate one time in order to achieve access to multiple applications, machines, and domains operating with a variety of authentication mechanisms
- It provides unified login experience when accessing one or multiple systems
- Also known as federated ID Typical SSO architecture management
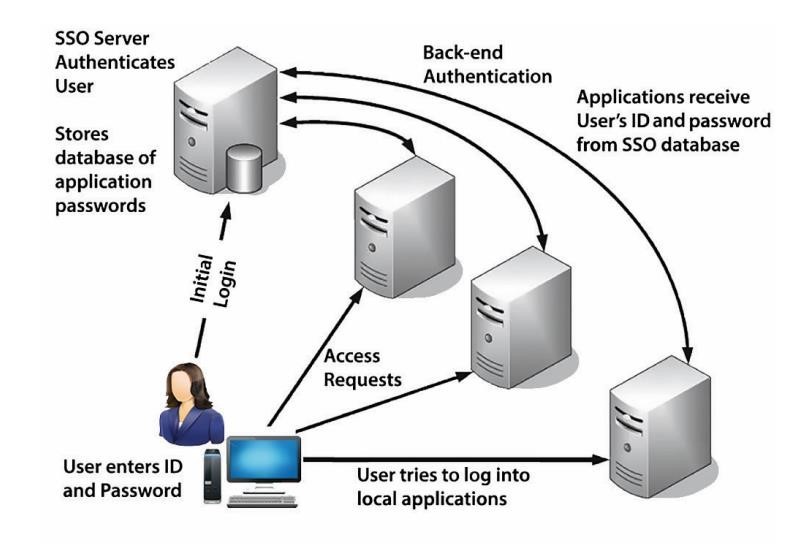
Federated Identity Management
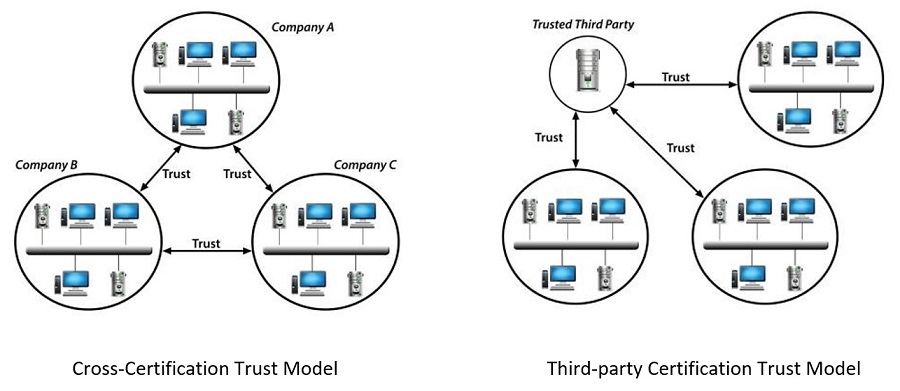
Cross-Certification Trust Model Third-party Certification Trust Model
Kerberos
- Kerberos is a network authentication protocol
- It is designed to provide strong authentication for client/server applications by using secret-key cryptography
- It guards a network with authentication, authorization and auditing
- Kerberos is often used in distributed environments where users need a unique ID for each application on the network
Kerberos Architecture
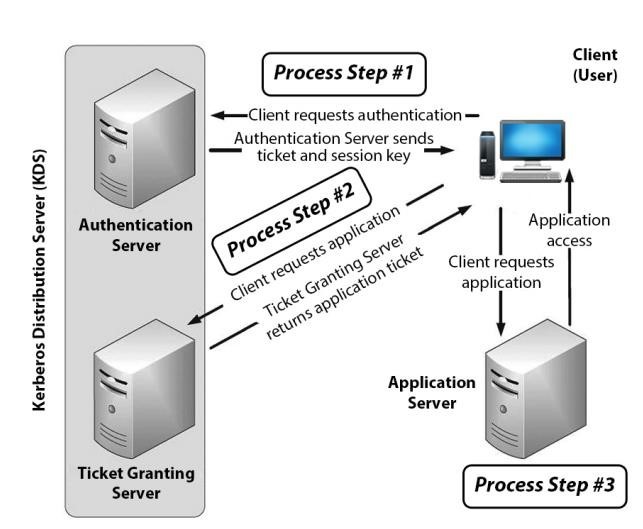
- Three components
- Requesting system (principal)
- Endpoint destination server
- Kerberos server
- Also called Kerberos distribution center (KDC)
- Authentication server
- Ticket granting server
- Kerberos uses symmetrical encryption with a shared key
SESAME
- SESAME offers sophisticated single sign-on with added distributed access control features and cryptographic protection of data
- SESAME is an extension of Kerberos using public key cryptography
- Uses public key cryptography to distribute symmetric keys
- Provides RBAC
- Uses Privileged Attribute Certificate (PAC) – similar to Kerberos ticket
SAML
- Security Assertion Markup Language (SAML) is a XML-based framework for creating and exchanging authentication and authorization between trusted entities over the Internet
- SAML allows business entities to make assertions regarding the identity, attributes, and entitlements of a subject entity (often a human user) to other entities, such as a partner company or another enterprise application
Source: NIST SP 800-63-2
Assertions
- In SAML, assertion is a package of security information
- Types of assertion statements
- Authentication statements
- Include information about the assertion issuer, the authenticated subject, validity period, and other authentication information
- For example, subject “John” was authenticated using a password at 10:32pm on 06-06-2004
- Attribute statements
- Contain specific additional characteristics related to the subject
- For example, subject “John” is associated with attribute “Role” with value “Manager”
- Authorization statements
- A request to allow the specified subject to access the specified resource has been granted or denied
- For example, subject “John” for action “Read” on “Webserver1002” given evidence “Role”
Source: Oasis-open.org
How SAML Works
- SAML defines three roles:
- Principal - typically a user
- Identity Provider (IdP) - who “asserts” the identity of the user
- Service Provider (SP) - who consumes the “assertion”
Source: Oasis-open.org
How SAML Works
- The principal requests a service from the service provider
- The service provider requests and obtains an identity assertion from the identity provider
- Before delivering the identity assertion to the SP, the IdP may request some information from the principal – such as a username and password – in order to authenticate the principal
- On the basis of this assertion, the service provider can make an access control decision i.e., decide whether to perform the service for the connected principal
- One IdP may provide SAML assertions to many SPs. Similarly, one SP may rely on and trust assertions from many independent IdPs
Source: Oasis-open.org
SAML Components
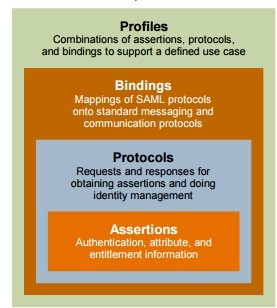
- Building-blocks
- Assertions XML schema - define the structure of the assertion
- SAML Protocols - used to request assertions and artifacts
- Bindings - define the underlying communication protocols (such as HTTP or SOAP) and that can be used to transport the SAML assertions
- Profiles - define constraints and/or extensions in support of the usage of
SAML for a particular application Source: Oasis-open.org
SAML Use Cases
- Web Single Sign-On
- SAML enables web SSO through the communication of an authentication assertion from one website to another website
- Attribute-Based Authorization
- The attribute based authorization model has one web site communicating identity information (a subject’s attributes and characteristics) to another web site in support of some transaction
Source: Oasis-open.org
SAML SSO
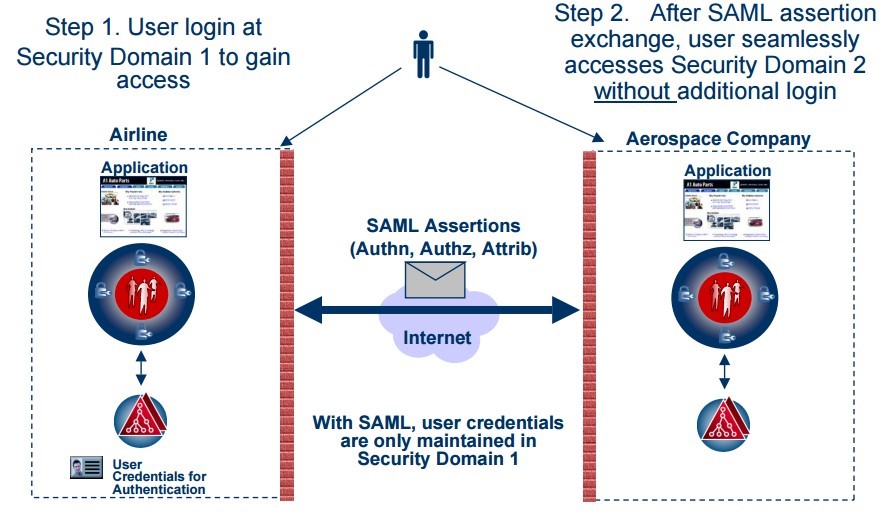
Source: http://csrc.nist.gov/archive/pki-twg/y2003/presentations/twg-03-13.pdf
SP Initiated SAML SSO
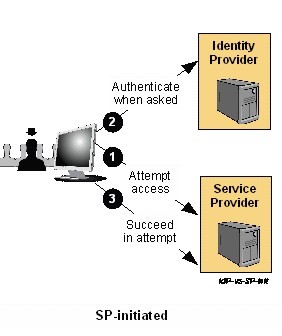
- User chooses a browser bookmark or clicks a link that takes them directly to an SP application resource they needs to access
- The user is not logged in at the SP yet. Hence the SP sends the user to an IdP to authenticate
- The IdP builds an assertion representing the user's authentication at the IdP and then sends the user back to the SP with the assertion
- The SP processes the assertion and determines whether to grant the user access to the resource
Source: Oasis-open.org
IdP Initiated SAML SSO
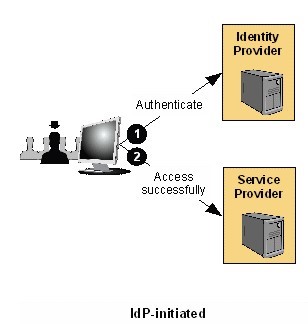
- User visits an IdP where they are already authenticated and they click on a link to a partner SP
- The IdP builds an assertion representing the user's authentication state at the IdP and
- The IdP them sends the user's browser over to the SP's assertion consumer service, which processes the assertion and creates a local security context for the user at the SP
Source: Oasis-open.org
Monitoring
- Detect any deviation from established access control policies
- Record
- Authentication process
- Authentication attempts
- Rights usage
- Rights access and denial
- Monitor status of controls
Access Control Assurance
- Audit Trail Monitoring
- Audit event types: network, system, application, user, keystroke
- Auditing issues
- Control volume of data
- Clipping levels (amount of info)
- Protect logs against unauthorized access/changes
- Store/archive securely
©Bipin Prabhakar. All rights reserved. 56
Audit Logs
- Audit logs are necessary in the event an action must be traced back to a user
- Collected from IDS, servers, firewalls, and other network devices
- Stored in a Security Information and Event Management (SIEM) system for analysis through tools
- Retention policy
Advanced IAM Offerings
Hype Cycle for IAM Technologies
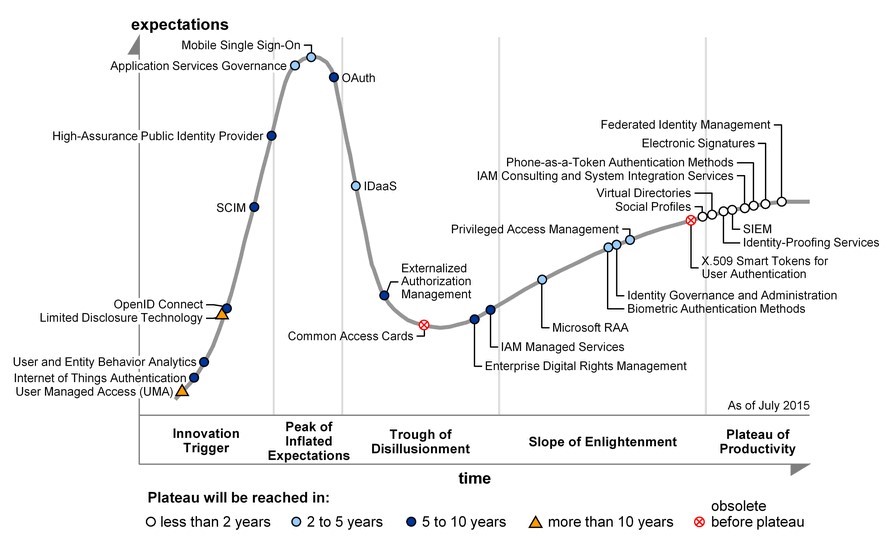
Source: Gartner (July 2015)
Identity Management in Cloud
- Unauthorized access to sensitive information in public, private, and hybrid clouds is a major security concern
- Need to specify IAMs in terms of identity proofing, strength of credentials, and access control mechanisms for effective federal cloud-based authentication and authorization
- To achieve effectiveness and scalability, seamless extension of controls from agencies to the cloud is needed
- Establishing trust relationships between cloud customers and cloud providers and potentially identity, credential, and attribute providers is key
Source: NIST SP500-2913
Identity Management in Cloud
- The cloud-subscriber requires to provision user accounts for cloud-subscriber-users to access the cloud. Also the cloud-subscriber requires the synchronization of enterprise system-wide user accounts from enterprise data center-based infrastructure to the cloud
- The cloud-subscriber-user should be able to transparently log in to the cloud application/service after authentication using standard protocols like SAML or Kerberos
- A cloud-subscriber-administrator should be able to manage (add/delete/change) data access authorization policies for data stored in the cloud
- The cloud-subscriber requires changes to user credentials in the enterprise's identity provider system to be automatically communicated to the corresponding infrastructure in the cloud-provider's system to ensure the integrity of access and conformance to enterprise policies are maintained
- Conduct ongoing automated monitoring of the cloud-provider infrastructure to demonstrate compliance with cloud-subscriber security policies and auditing requirements
Source: NIST SP500-2913
Identity as a Service
- Identity-as-Service (IDaaS) offerings are cloud-based services that broker identity and access management functions to target systems on customers’ premises and in the cloud.
- IDaaS is described as a combination of administration and account provisioning, authentication and authorization, and reporting functions
IDaaS Functionality
- IDaaS functionality includes:
- Identity governance and administration (IGA) — this includes the ability to provision identities held by the service to target applications
- Access — this includes user authentication, single sign-on, and authorization enforcement
- Intelligence — this includes logging events and providing reporting that can answer questions, such as who accessed what and when
Summary
Appendix
User identifiers in Windows OS
- Every Windows user, computer, or service account has a unique security identifier (SID) and the relative identifier (RID)
- Windows security-related processes use SIDs to uniquely identify security principles
- A SID is unique in the environment where it was created and in time
- A few well-knows SIDs
- SID: S-1-1-0
- Name: Everyone
- Description: A group that includes all users, even anonymous users and guests. Membership is controlled by the operating system
- SID: S-1-5-21domain-500
- Name: Administrator
- Description: A user account for the system administrator. By default, it is the only user account that is given full control over the system
- SID: S-1-5-21domain-501
- Name: Guest
- Description: A user account for people who do not have individual accounts. This user account does not require a password. By default, the Guest account is disabled
LDAP Hierarchy
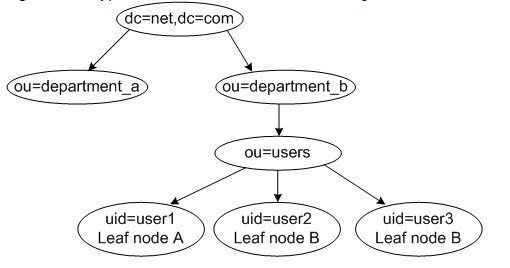
- The DNs of the three leaf nodes in the figure are
- uid=user1,ou=users,ou=depar tment_b,dc=net,dc=com
- uid=user2,ou=users,ou=depar tment_b,dc=net,dc=com
- uid=user3,ou=users,ou=depar tment_b,dc=net,dc=com
- To create a DN in an LDAP directory, cascade the complete path from the leaf node to the root node
Source: http://support.huawei.com/
Kerberos Process
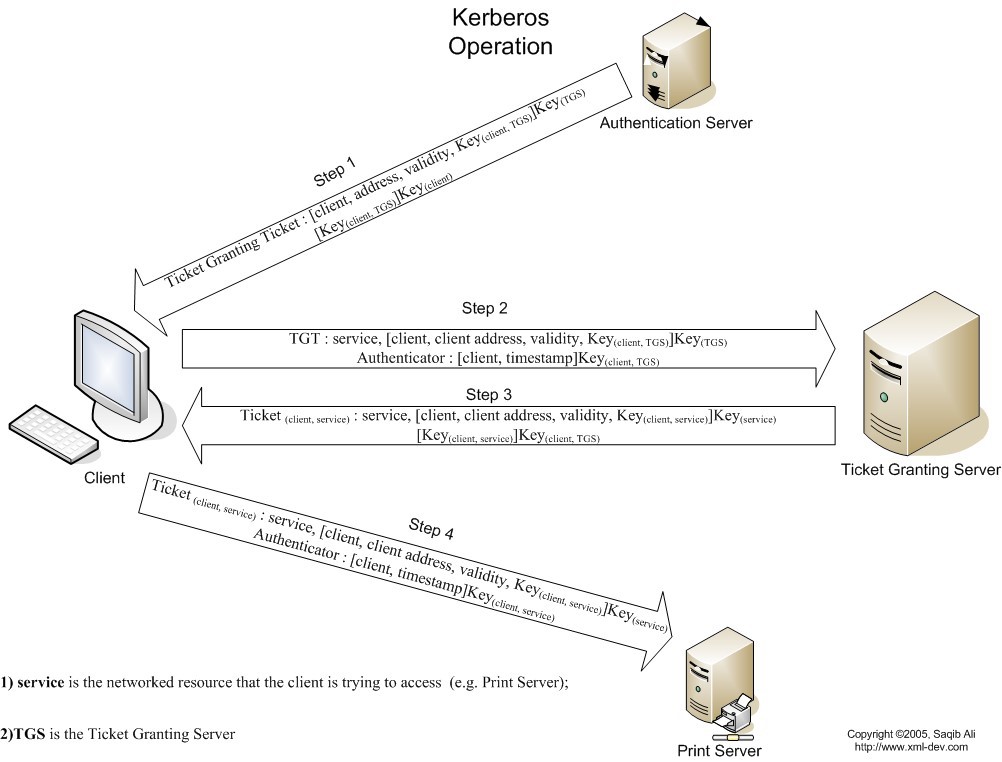
- Read source link for details
ABAC – Detailed Architecture
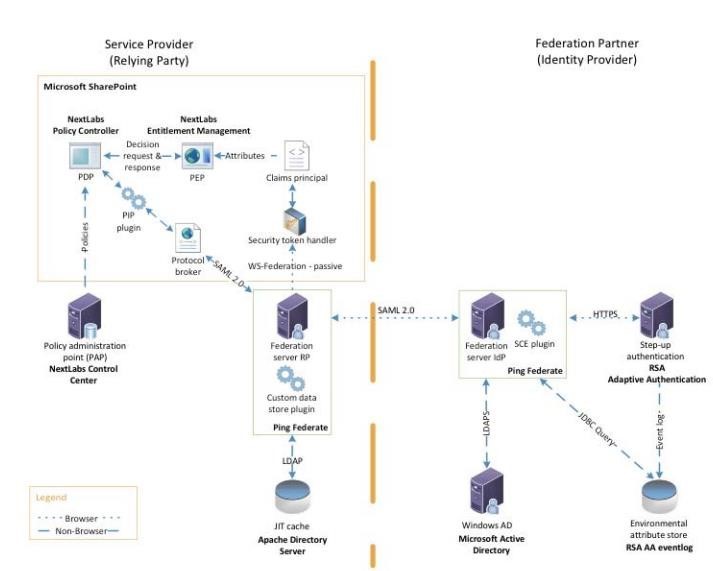
Source: NIST SP1800-3b - ABAC
Facial Imaging
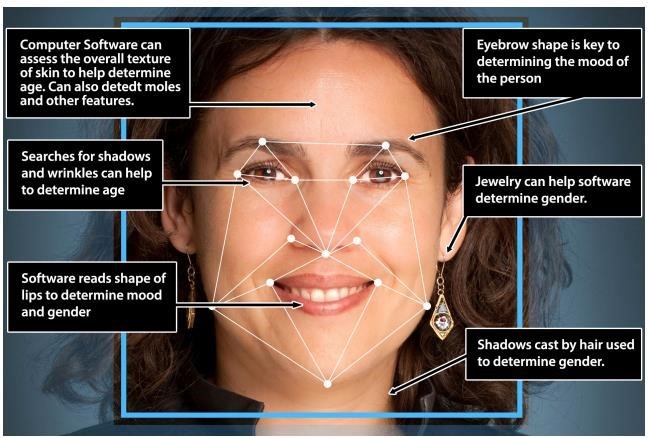
Geometric properties of a subject’s face used in Facial Imaging
Iris Patterns and Retinal Scanning
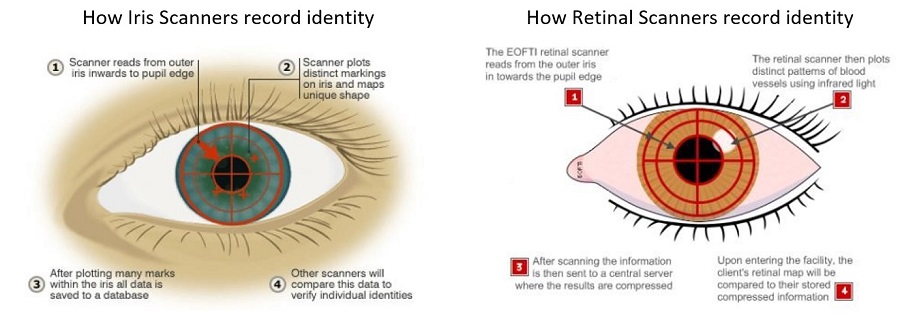
How Iris Scanners record identity How Retinal Scanners record identity
Ref:
http://news.bbc.co.uk/2/shared/spl/hi/guides/456900/456993/html/nn3page1.stm
Ref: http://www.eofti.com/about/retinal-scan/Behavioral Patterns
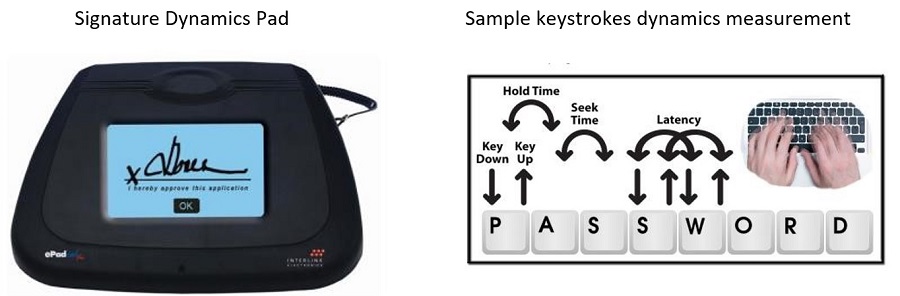
Signature Dynamics Pad Sample keystrokes dynamics measurement
Ref: http://bit.ly/ePadAPIs Ref: http://bit.ly/typeprint_technology
Gartner’s Magic Quadrant for IDaaS
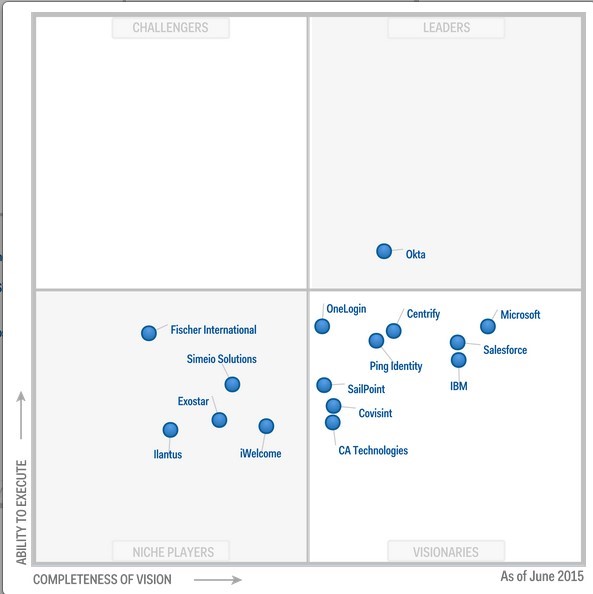
Source: Gartner
Example of how IAM roles are defined in AWS
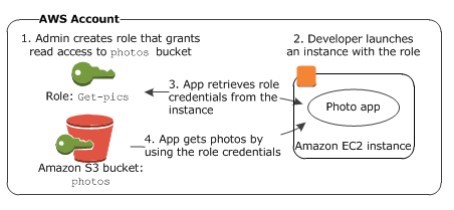
- An administrator uses IAM to create the Getpics In the role, the administrator uses a policy that specifies that only Amazon EC2 instances can assume the role and that specifies only read permissions for the photos bucket.
- A developer launches an Amazon EC2 instance and associates the Get-pics role with that instance.
- When the application runs, it retrieves credentials from the instance metadata on the Amazon EC2 instance.
- Using the role credentials, the application accesses the photo bucket with read-only permissions.
Source: AWS: Overview of Security Processes
Identity Federation in AWS
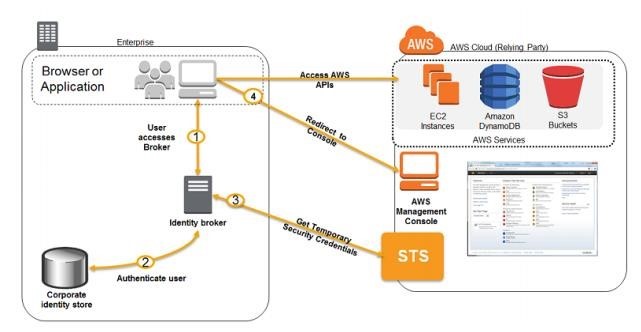
Source: AWS: Overview of Security Processes
References
- “Guide to Selecting Information Technology Security Products.” NIST SP 800-36
- “Guide to Attribute Based Access Control (ABAC) Definition and Considerations.” NIST SP 800-162
- “Cloud Computing Technology Roadmap Volume I.” NIST SP 500-293
- Richard Kuhn, Edward J. Coyne, Timothy R. Weil. “Adding Attributes to RoleBased Access Control”, IEEE Computer, vol. 43, no. 6 (June, 2010) , pp. 79-81’
- “Magic Quadrant for Identity and Access Management as a Service.” June 2015
- “2016 Planning Guide for Identity and Access Management.” October 2015
- “Overview of Security Processes.” Amazon Web Services. August 2015
- “Attribute Based Access Control.” NIST SP1800-3b


