Communications and Network Security Part 3
{`
Kelly School of Business
Indiana University
Information Systems Graduate Programs
`}
Part 3 - Multiprotocol and Multimedia Communication Security
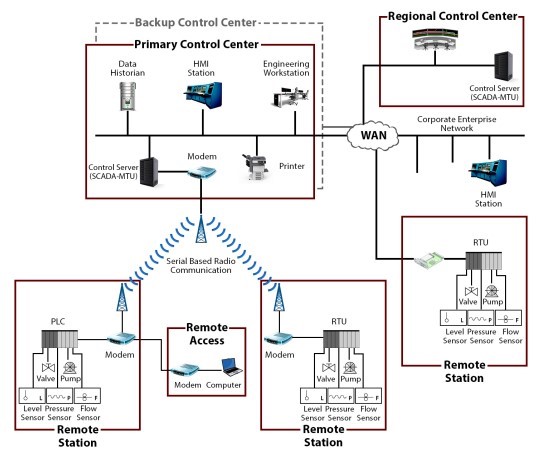
Industrial Control System (ICS)
- Industrial Control System (ICS) is a general term that encompasses several types of control systems including:
- Supervisory Control and Data Acquisition (SCADA) systems
- Distributed Control Systems (DCS)
- Other control system configurations such as skid-mounted Programmable
Logic Controllers (PLC)
Source: NIST SP 800-82
SCADA
- An assembly of interconnected equipment used to monitor and control physical equipment in industrial environments
- Largest subgroup of ICS systems and large scale processes that can include multiple sites and large distances
- These systems are used in critical infrastructure and distribution systems such as water distribution and wastewater collection systems, oil and natural gas pipelines, electrical utility transmission and distribution systems, nuclear power plants, and rail and other public transportation systems
IT Systems Vs. ICS
- Different Performance and Reliability Requirements
- Use of operating systems and applications that may be considered unconventional in typical IT
- Different Risk Management Requirements
- Physical interaction with environment
Source: NIST 800-82
ICS Security Incidents
- Threat agents
- Criminal groups, foreign intelligence services, terrorist groups, phishers, spammers, industrial spies, insiders
- Categories of incidents
- Intentional targeted attacks such as gaining unauthorized access to files, performing a DoS, or spoofing e-mails (i.e., forging the sender’s identity for an e-mail)
- Unintentional consequences or collateral damage from worms, viruses or control system failures
- Unintentional internal security consequences, such as inappropriate testing of operational systems or unauthorized system configuration changes
Source: NIST 800-82
ICS Security Objectives
- Restricting logical access to the ICS network and network activity
- Restricting physical access to the ICS network and devices
- Protecting individual ICS components from exploitation
- Maintaining functionality during adverse conditions
ICS Security Challenges
- Real time constraints - IT security technology can impact timing, inhibit performance (response times are on the order of ms to s)
- Balancing of performance, reliability, flexibility, safety, security requirements
- Difficulty of specifying requirements and testing capabilities of complex systems in operational environments
- Security expertise and domain expertise required, but are often separated
- Multiple device and vendor ‘backdoors’
- Ecosystem becoming more complicated with rapidly growing industrial
internet of things Source: NIST SP 800-82
Multimedia Communication - Voice
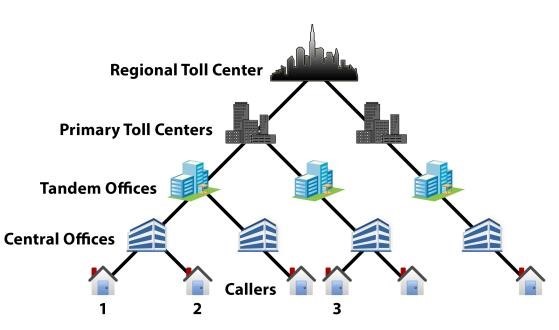
- Public Switched Telephone Network
(PSTN)
- Designed for analog voice communication
- Circuit switched network
- PSTN was easily exploited through tone-frequency attacks to make free calls, gain unauthorized access to voicemail systems, and manipulated
phone switches through PSTN hierarchy - a call between callers 1
and 3 must be switched within the leftmost primary toll office
ISDN
- Integrated Services Digital Network (ISDN)
- Digital transmission of voice and data
- Circuit switched network
- Still largely used for remote connectivity applications
- Susceptible to physical and router attacks
Voice over IP (VoIP)
- Allows transmission of voice traffic over IP-based networks
- Packet switched network
- Voice is converted into packets of data and then transmitted to the recipient over the Internet and decoded back into voice at the other end
- These packets are compressed before transmission with certain codecs; each codec has its own bandwidth requirements and provides different voice quality for VoIP calls
- Uses protocols like RTP, SIP, H.323, MGCP, SCCP, Skype
How VoIP works
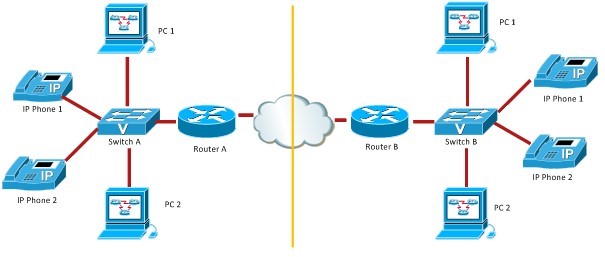
Source: Network World
Voice over IP (VoIP)
- IP Telephony
- Provides the full suite of VoIP enabled services including the interconnection of phones for communications, billing plans, and basic features such as conferencing, transfer, forward, and hold
- Unified Communications
- Encompasses a wide range of collaboration services, including IP telephony, web conferencing, telepresence, contact center, instant messaging, fax, presence information, mobility features, desktop sharing, etc.
- Cisco WebEx, Lync, Skype, FaceTime, Avaya Aura
Security Threats with VoIP
- Eavesdropping of phone conversation
- Intercepting voice packets and converting them into audio files
- Registration hijacking
- Attackers take control of the end points by registering them to rogue servers
- VoIP denial of service attacks
- Create large number of call setup requests and overwhelming the VoIP servers/end points, thereby crashing them and eventually bringing down the telephony system
Security Threats with VoIP
- Caller ID spoofing
- Disguising the name and phone number of the calling party; made easier and cheaper through VoIP
- Commonly used for phishing attacks
- Spam over Internet Telephony (SPIT)
- Unsolicited bulk messages broadcast over VoIP
- Poses bigger threat than email spam
- Service abuse threats
- Toll fraud, billing avoidance
Securing VoIP
- Create separate VLANs for data and voice
- Deploy VoIP-aware firewalls at the perimeter
- Use SRTP (Secure RTP) for encrypting both signaling and media
- Establish VPN tunnels for any endpoint connectivity outside of the corporate office
- Perform user and device authentication – use of PINs, certificates
Multimedia Communication – Instant Messaging
- Real time text transmission over internet
- Most instant messaging applications offer additional services like, screen sharing, remote control, exchange of files, and audio
- Originally, IM required installation of client software on the desktop, but current versions use web-based scripts based upon JavaScript and ActiveX. These scripts can be exploited to contact other users, send files, change program settings, and/or execute potentially malicious actions
Internet Relay Chat (IRC)
- Provides anonymity
- Popular in academia and underground organizations
- It is an unencrypted channel and hence an easy target for sniffing attacks
- It is also a common platform for social engineering attacks
Extensible Messaging and Presence Protocol (XMPP)
- Open standard IM protocol formalized by IETF
- Commonly used protocol for Internet of Things applications
- Does not support end to end encryption
- Anybody can host an XMPP server; hence trust a server only if its certificate has been validated by a valid certificate authority
Virtualized Networks
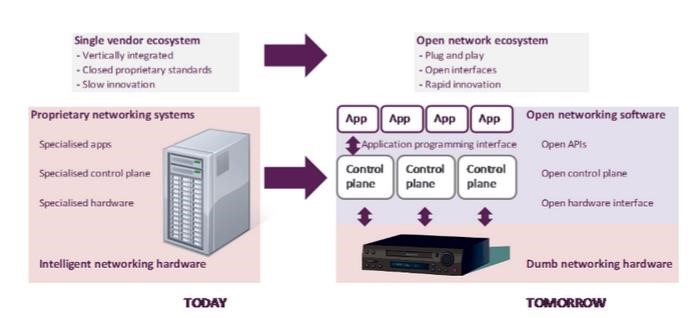
- ‘Abstraction’
- Move from proprietary networking systems (eg. Cisco IOS, Junos) to open software
Source: CM Research
Software Defined Networking (SDN)
- org defines SDN as “the physical separation of the network control plane from the forwarding plane, and where a control plane controls several devices”
- Network infrastructure is abstracted from the application
- SDN separates traditional network traffic into three components: raw data (infrastructure layer), how the data is sent (control layer),
and what purpose the data serves (application layer)
SDN Planes
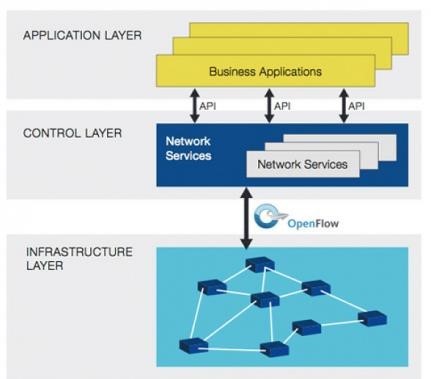
- Infrastructure Layer (Data Plane) – Network switches and routers and the data itself as well as the process of forwarding data to the appropriate destination
- Control Layer (Control Plane) – The intelligence in devices that works in true “middle-man” fashion, determining how traffic should flow based on the status of the infrastructure layer and the requirements specified by the application layer
- Application Layer (Application Plane) – Network services, utilities, and applications that interface with the control level to specify Source: opennetworking.org needs and requirements
SDN and Security Attributes
- SDN is ideal for security processing because it offers an end-to-end, service-oriented connectivity model that is not bound by traditional routing constraints
- Logically centralized control allows for effective performance and threat monitoring across the entire network
- Granular policy management can be based on application, service, organization, and geographical criteria rather than physical configuration
- Dynamic and flexible adjustment of security policy is provided under programmatic control
- Flexible path management achieves rapid containment and isolation of intrusions without impacting other network users
Source: opennetworking.org
SDN Security Challenges
- The centralized controller emerges as a potential single point of attack and failure that must be protected from threats
- Control flow saturation attack – a SDN DoS
- ‘Rogue’ controller
- Exploiting APIs
- REST API has a default password which is trivial. If an SDN deployment didn’t change this default password, the attacker can create his own SDN policies and thus gain control of the SDN environment
- Not as ‘mature’ as the traditional networking system
Source: opennetworking.org
Reference
- Official (ISC)2 Guide to the CISSP CBK, Fourth Edition ISC2 Press
- NIST 800-82
- SANS - Understanding Instant Messaging (IM) and its security risks
- SANS - VoIP Security Vulnerabilities
- Open Networking Foundation - SDN Security Considerations in the Data Center
Appendix
A Generic SCADA system