CCNA Exercise Lab 9
Written Lab
In this section, write the answers to the following questions:
1. Configure a standard IP access list to prevent all machines on network 172.16.0.0 from accessing your Ethernet network.
Ans- #access-list 10 deny 172.16.0.0
2. Apply the access list to your Ethernet interface.
Ans- #conf t
#int eth0/0
#access-list 10 -------
3. Create an access list that denies host 196.22.15.5 access to your Ether- net network.
Ans- #access-list 11deny 196.22.15.5 0.0.0.0
4. Write the command to verify that you’ve entered the access list correctly.
Ans- #show access-list
5. Write the two commands that verify the access list was properly applied to the Ethernet interface.
Ans- #show access-list
#show ip access-list
6. Create an extended access list that stops host 172.16.10.1 on Ethernet 0 from telnetting to host 172.16.30.5 on Ethernet 1.
Ans- # access-list 101 deny tcp host 172.16.10.1 int eth0 host 172.16.30.5 int eth1 eq telnet
7. Apply the access list to the correct interface.
8. Configure an IPX SAP access list that prevents any file service SAP messages other than those from IPX address 45.0000.0000.0001 from leaving the Ethernet 0 network.
Ans- #ip access-list ipxsap
#interface ethernet 0/0
#access-list deny any any
#access-list perit 45.0000.0000.0001 0.0.0.0
9. Apply the IPX SAP access list to the Ethernet interface.
Hands-on Labs
In this section, you will complete three labs. To complete these labs, you will need at least three 2500 series routers, or the RouterSim product.
Lab 9.1: Standard IP Access Lists Lab
9.2: Extended IP Access Lists Lab
9.3: Standard IPX Access Lists
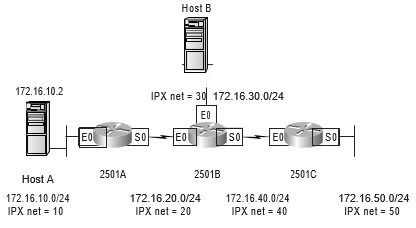
All of the labs will use Figure 9.3 for configuring the routers.
FIGURE 9.3 Access list lab figure
Lab 9.1: Standard IP Access Lists
In this lab, you will allow only Host B from network 172.16.30.0 to enter network 172.16.10.0.
- Go to 2501A and enter global configuration mode by typing config t.
- From global configuration mode, type access-list? to get a list of all the different access lists
- Choose an access list number that will allow you to create an IP standard access This is a number between 1 and 99.
- Choose to permit host 172.16.30.2:
2501A(config)#access-list 10 permit 172.16.30.2?
A.B.C.D Wildcard bits
To specify only host 172.16.30.2, use the wildcards 0.0.0.0:
RouterA(config)#access-list 10 permit 172.16.30.2
0.0.0.0 - Now that the access list is created, you must apply it to an interface to make it work:
2501A(config)#int e0
2501A(config-if)#ip access-group 10 out - Verify your access lists with the following commands:
RouterA#sh access-list
Standard IP access list 10 permit 172.16.30.2
RouterA#sh run
-cut-
interface Ethernet0
ip address 172.16.10.1 255.255.255.0
ip access-group 10 out ipx network 10A - Test your access list by pinging from Host B (172.16.30.2) to Host A (172.16.10.2).
- Ping from 2501B and 2501C to Host A (172.16.10.2); this should fail if your access list is correct.
Lab 9.2: Extended IP Access Lists
In this lab, you will use an extended IP access list to stop host 172.16.10.2 from creating a Telnet session to router 2501B (172.16.20.2). However, the host still should be able to ping the 2501B router. IP extended lists should be placed closest to the source, so add the extended list on router 2501A.
- Remove any access lists on 2501A and add an extended list to 2501A.
- Choose a number to create an extended IP list. The IP extended lists use 100–199.
- Use a deny statement (you’ll add a permit statement in step 7 to allow other traffic to still work).
2501A(config)#access-list 110 deny?
< 0-255 > An IP protocol number
ahp Authentication Header Protocol
eigrp Cisco's EIGRP routing protocol esp Encapsulation Security Payload
gre Cisco's GRE tunneling
icmp Internet Control Message Protocol
igmp Internet Gateway Message Protocol
igrp Cisco's IGRP routing protocol
ip Any Internet Protocol
ipinip IP in IP tunneling
nos KA9Q NOS compatible IP over IP tunneling
ospf OSPF routing protocol pcp Payload Compression Protocol
tcp Transmission Control Protocol
udp User Datagram Protocol - Since you are going to deny Telnet, you must choose TCP as a Transport layer protocol:
2501A(config)#access-list 110 deny tcp?
A.B.C.D Source address any Any source host
host A single source host - Add the source IP address you want to filter on, then add the destina- tion host IP address. Use the host command instead of wildcard bits.
2501A(config)#access-list 110 deny tcp host
172.16.10.2 host 172.16.20.2?
ack Match on the ACK bit
eq Match only packets on a given port number
established Match established connections fin Match on the FIN bit fragments Check fragments
gt Match only packets with a greater port number
log Log matches against this entry log-input Log matches against this entry,
including input interface
lt Match only packets with a lower port number
neq Match only packets not on a given port number
precedence Match packets with given precedence value
psh Match on the PSH bit
range Match only packets in the range of port numbers
rst Match on the RST bit
syn Match on the SYN bit
tos Match packets with given TOS value
urg Match on the URG bit
- At this point, you can add the eq telnet command. The log command can also be used at the end of the command so that whenever the access-list line is hit, a log will be generated on the console.
2501A(config)#access-list 110 deny tcp host
172.16.10.2 host 172.16.20.2 eq telnet log - It is important to add this line next to create a permit statement.
2501A(config)#access-list 110 permit ip any 0.0.0.0
255.255.255.255 - Apply the access list to the Ethernet 0 on 2501A to stop the Telnet traffic as soon as it hits the first router interface.
RouterB(config)#int e0
RouterB(config-if)#ip access-group 110 in
RouterB(config-if)#^Z - From host 172.16.10.2: >telnet 172.16.20.2
On Router B’s console, this should appear as follows:
01:11:48: %SEC-6-IPACCESSLOGP: list 110 denied tcp
172.16.10.2(1030) -> 172.16.20.2(23), 1 packet
01:13:04: %SEC-6-IPACCESSLOGP: list 110 denied tcp
172.16.10.2(1030) -> 172.16.20.2(23), 3 packets
Lab 9.3: Standard IPX Access Lists
In this lab, you will configure IPX to allow only IPX traffic from IPX Net- work 30 and not from IPX Network 50.
- Remove any existing access lists on the 2501A router. Because this is an IPX standard access list, the filtering can be placed anywhere on the network since it can filter based on IPX source and destination IP addresses.
- Verify that you have the IPX network working as shown in Figure 3. Use the show ipx route command to see all networks on your routers.
- Configure an access list on 2501A to allow only IPX traffic from Net- work 30 and to deny IPX Network 50. IPX standard lists use the access list numbers 800–899.
2501A#config t
RouterC(config)#access-list 810?
deny Specify packets to reject
permit Specify packets to permit - First, deny IPX Network 50, then permit everything else. The –1 is a wildcard in IPX.
2501A(config)#access-list 810 deny?
-1 Any IPX net
< 0-FFFFFFFF > Source net
N.H.H.H Source net.host address - Choose Network 30 as a source address:
2501A(config)#access-list 810 deny 50
-1 Any IPX net
<0-FFFFFFFF>Destination net
N.H.H.H Destination net.host address
< cr > - Choose Network 10 as the destination network:
2501A(config)#access-list 810 permit 50 10 - Permit everything else with an IPX wildcard:
2501A(config)#access-list 810 permit –1 -1 - Apply the list to the serial interface of 2501A to stop the packets as they reach the router:
2501A(config)#int s0
2501A(config-if)#ipx access-group 810 in
2501A(config-if)#^Z - Verify the list by looking at the IPX routing table. Network 50 should not be in the 2501A IPX routing table. Also, use the show access- list and show ipx access-list commands to vary the list.
Review Questions
1. IP standard access lists use which of the following as a basis for permitting or denying packets?
- Source address
- Destination address
- Protocol
- Port
- Ans- A
2. IP extended access lists use which of the following as a basis for per- mitting or denying packets?
- Source address
- Destination address
- Protocol
- Port
- All of the above
- Ans- E
3. To specify all hosts in the Class B IP network 172.16.0.0, which wild- card access list mask would you use?
- 255.255.0.0
- 255.255.255.0
- 0.0.255.255
- 0.255.255.255
- 0.0.0.255
- Ans- C
4. Which of the following are valid ways to refer only to host 172.16.30.55 in an IP access list?
- 172.16.30.55 0.0.0.255
- 172.16.30.55 0.0.0.0
- any 172.16.30.55
- host 172.16.30.55
- 0.0.0.0 172.16.30.55
- ip any 172.16.30.55
- Ans- A
5. Which of the following access lists will allow only WWW traffic into network 196.15.7.0?
- access-list 100 permit tcp any 196.15.7.0 0.0.0.255 eq www
- access-list 10 deny tcp any 15.7.0 eq www
- access-list 100 permit 15.7.0 0.0.0.255 eq www
- access-list 110 permit ip any 15.7.0 0.0.0.255
- access-list 110 permit www 196.15.7.0 0.0.0.255
- Ans- C
6. Which of the following commands will show the ports that have IP access lists applied?
- show ip port
- show access-list
- show ip interface
- show access-list interface
- show running-config
- Ans- B
7. What wildcard would you use to filter networks 172.16.16.0 through 172.16.23.0?
- 172.16.16.0 0.0.0.255
- 172.16.255.255 255.255.0.0
- 172.16.0.0 0.0.255.255
- 172.16.16.0 0.0.8.255
- 172.16.16.0 0.0.7.255
- 172.16.16.0 0.0.15.255
- Ans- E
8. Which of the following is a valid IPX standard access list?
- access-list 800 permit 30 50
- access-list 900 permit 30 50
- access-list permit all 30 50
- access-list 800 permit 30 50 eq SAP
- access-list 900 permit –1 50
- Ans- D
9. What wildcard would you use for the following networks? 172.16.32.0 through 172.16.63.0
- 172.16.0.0 0.0.0.255
- 172.16.255.255 0.0.0.0
- 0.0.0.0 255.255.255.255
- 172.16.32.0 0.0.0.255
- 172.16.32.0 0.0.0.31
- 172.16.32.0 0.0.31.255
- 172.16.32.0 0.31.255.255
- 172.16.32.0 0.0.63.255
- Ans- F
10. Which of the following commands will apply IPX SAP access list 1050 for incoming traffic, assuming you’re already at interface configuration?
- ipx access-group 1050 in
- ipx input-sap-filter 1050
- ipx access-list 1050 in
- ipx input-sap-filter 1050 in
- ipx access group1050
- Ans- D
11. Which of the following commands will show extended access list 187?
- sh ip int
- sh ip access-list
- sh access-list 187
- sh access-list 187 extended
- Ans- C
12. What is the IP extended access list range?
- 1–99
- 200–299
- 1000–1999
- 100–199
- Ans- D
13. Which of the following commands is valid for creating an extended IP access list?
- access-list 101 permit ip host 16.30.0 any eq 21
- access-list 101 permit tcp host 172.16.30.0 any eq 21 log
- access-list 101 permit icmp host 172.16.30.0 any ftp log
- access-list 101 permit ip any eq 16.30.0 21 log
- Ans- A
14. What is the extended IPX access list range?
- 100–199
- 900–999
- 1000–1999
- 700–799
- Ans- B
15. What does the –1 mean in an extended IPX access list?
- Deny this host
- Deny any network or host
- Local network only, no hops
- Any host or any network
- Ans- D
16. What are three commands you can use to monitor IP access lists?
- sh int
- sh ip interface
- sh run
- sh access-list
- Ans- A,B,D
17. Which of the following commands should follow this command? access-list 110 deny tfp any any eq ftp
- access-list 110 deny ip any any
- access-list 110 permit tcp any any
- access-list 110 permit ip any
- access-list 110 permit ip any 0.0.0.0 255.255.255.255
- Ans- B
18. Which access configuration allows only traffic from network 172.16.0.0 to enter int s0?
- Access-list 10 permit 172.16.0.0 0.0.255.255, int s0, ip access-list 10 in
- Access-group 10 permit 172.16.0.0 0.0.255.255, int s0, ip access-list 10 out
- Access-list 10 permit 172.16.0.0 0.0.255.255, int s0, ip access-group 10 in
- Access-list 10 permit 172.16.0.0 0.0.255.255, int s0, ip access-group 10 out
- Ans- C
19. Where should you place standard access lists in a network?
- On the closest switch
- Closest to the source
- Closest to the destination
- On the Internet
- Ans- C
20. Where should you place extended access lists in a network?
- On the closest switch
- Closest to the source
- Closest to the destination
- On the Internet
- Ans- B


