Sample Homework : Capstone Project SRS
1. Introduction
1.1 Purpose
This document describes the software requirements and other related details of the Sales Database created by the team on MS Access for Global Bike Incorporated (GBI). The purpose of the dashboard is to allow the corporation manage, related and view their data easily, with the ability to view reports, and tables, and form appropriate relations between the tables in order to view a pictorial representation of sales and other trends. Th project offers GBI a software that is concise and compact as compared to their current system, and is able to build required tables, generate forms to input data, create queries to access those data, and generate a report. This is the first version of this document.
1.2 Document Conventions
The document throughout has been written with no spacing, 11 point, Times New Roman font, with headings of 14 point and numbered to distribute sections. Priorities for higher-level requirements have been assumed to be inherited by detailed requirements gathered through research done by the team to gather GBI’s necessities for the software solution. All requirements have their own priority but some requirements have been considered more important than others.
1.3 Intended Audience and Reading Suggestions
The SRS is intended to be read by the IT personnel of the GBI corporation, who will be in charge of operating the software, thus are the users and testers, project managers, who will relay the requirements to upper management, documentation writers who will work further on this document to create related documentation.
This document is divided into 5 sections:
- Introduction, which included the generic data about the software like scope and document conventions.
- Overall description that focuses on the user documentation and design and implementation constraints.
- External Interface Requirements address software, hardware, communication and user interfaces.
- System features describe the operations that the software can perform and the features it has.
- Other Nonfunctional Requirements addresses things like business rules, SQA etc.
The sequence in which the document should be read is the sequence it has been defined in the table of contents, generically. However, for the IT personnel, the External Interface Requirements and System Features are the most pertinent read, given that they have to work on the set up of the system. While for the project managers, reading the overall description and scope of the software, the user documentation, and Other-Nonfunctional Requirements is of much more interest given that they need to assess the requirements provided by the client.
1.4 Product Scope
The specified project is a Stakeholder Sales Dashboard, which will have the following features:
- Create database tables
- Establish table relationships
- Generate a form to input data
- Build queries to access data
- Generate a report
The software is supposed to present a cohesive solution to the GBI corporation in form of a dashboard that allows the user to input, manage and view data as required through queries. The software will help the information be more organized and correlated, with the benefit that the user will be able to view an organized representation of the data in form of a report. The system offers a centralized system that can be easily manipulated using single queries. The objective is to move from the old, redundant system to a solution that is more managed and cohesive in nature.
GBI wants its stakeholders to be able to view the data about the company’s operations and the progress as easily as possible, and this is what the software intends to provide, a simplified, organized representation of the data, which can be easily presented to the concerned stakeholders without hassle of having to collect the data from multiple places.
1.5 References
The document follows the IEEE format for the SRS document. The reference to document is as follows:
IEEE (2019). SRS template. [online] Web.cs.dal.ca. Available at: https://web.cs.dal.ca/~hawkey/3130/srs_template-ieee.doc [Accessed 5 May 2019].
2. Overall Description
2.1 Product Perspective
The need for the software arose as the current system for the GBI is slow, redundant, and is dispersed. The current system has data spreadsheets that have to be handled separately and disjointly by the different staff members based on what they oversee, where this data is often
shared via email and stored redundantly in excel spreadsheets across the department. This manner of storage often leads to hardships with regards to how the data was managed, updated, and shared; when data needs to be updated, all copies must be updated manually with great care so that out of date information is not kept and recirculated through the system. Thus, this new system is proposed to replace the current one.
This SRS describes the whole solution and is the solution is not a component of a larger system.
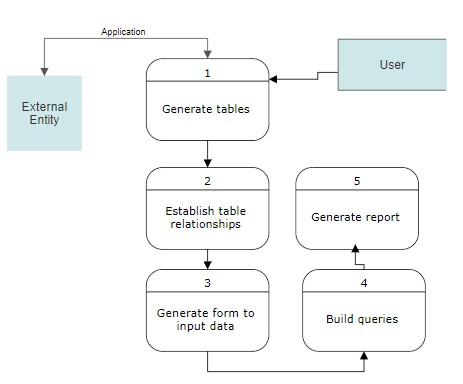
The diagram for the over view for the solution can be found in the Appendix.
2.2 Product Functions
The major functions that the software needs to the let the user perform are:
- Generate tables
- Form Queries
- Input and edit data
- Form relationships between the data
- Generate reports and appropriate pictorial representations of data
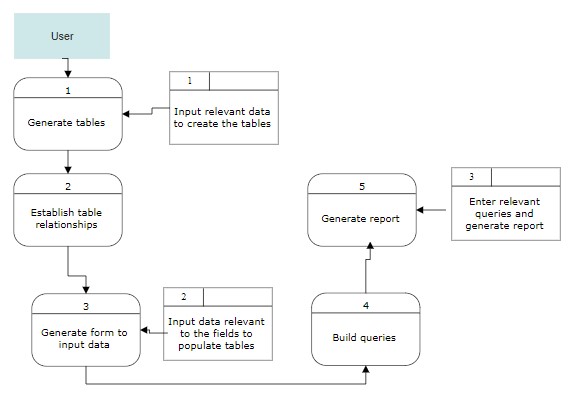
The DFD in appendix gives an overview of the data flow in the system per the software requirements.
2.3 User Classes and Characteristics
The user classes for this software are the following:
- Admin
- Order Department Personnel
- Managers
The admin will have rights to access the whole software and the data available in the software and be able to manipulate it any way possible. This user will be able to define the user rights of other users, and add or delete user access to the software accordingly; while the Order department personnel will be able to access and view only data and tables pertaining to the orders like customer table, order table and products table. The managers will also have access to most tables and data but not the whole functionality. The admin class is the more important one as they have rights to the whole system, then the managers have higher priority to the order department personnel, who have the least priority as users.
2.4 Operating Environment
The software will require the following hardware and software components to operate successfully:
|
Required Processor |
1 gigahertz (Ghz) or faster x86- or x64-bit processor with SSE2 instruction set |
|
Required Software |
Microsoft Access 2008 or above |
|
Required Operating System |
Windows 8, Windows 7, Windows Server 2008 R2, or Windows Server 2012 |
|
Required Memory |
1 GB RAM (32 bit); 2 GB RAM (64 bit) |
|
Required Hard Disk Space |
3.0 GB available |
|
Required Display |
Graphics hardware acceleration requires a DirectX10 graphics card and 1024 x 576 resolution |
|
.NET version |
3.5, 4.0, or 4.5 |
|
Required Browser |
Microsoft Internet Explorer 8, 9, or 10; Mozilla Firefox 10.x or a later version; or Google Chrome 17. x. |
The system requirements have been rounded up to the nearest 0.5 GB, to be conservative. For example, if the measure of an application’s required hard disk space to be 1.99 GB, it is recommended 2.5 GB of disk space. The hard disk system requirements mentioned here are intentionally larger than the actual disk space usage of the software.
2.5 Design and Implementation Constraints
There are hardly any design or implementation constraints in the software given that the proposed solution uses basic products that can be bought easily through Microsoft’s store. The company needs to buy licensed software for the MS Access Database and the Windows OS.
Other than that, all proposed hardware and software requirements are easily procurable and maintainable. MS Access requires a know-how of how the software operates for the end-user, as to how tables are created, managed. Added to that users need to learn how to write queries in order to manipulate the data tables and generate reports. Given that GBI personnel will be responsible to maintain the software, there is a need for basic training and understanding of how the software operates and is installed.
IF the user were to email from the MS Access program then there will be a constraint, i.e. Windows will interrupt the Mail Applications Programming Interface (MAPI) message and prompt user for confirmation.
2.6 User Documentation
Users will be provided with a user manual along with this SRS, which will also follow the IEEE format.
2.7 Assumptions and Dependencies
- The software operates on third-party software that is Microsoft Access, which requires a licensed buy to be able to use it for long-term.
- The software operates on the Windows OS, which also needs to be licensed.
- The software is not dependent on any other software solution or re-uses any component of any other software solution.
- It incorporates its sister solutions like MS Excel and MS Outlook to import tables and send emails, however, it does not need any additional plugins or protocols to operate with these programs.
3. External Interface Requirements
3.1 User Interfaces
The software has a very easy to use interface and allows users to be able to easily perform the proposed functions. Given that the software requires that the user have some know-how of how MS Access works, the solution should be able to be easily used and manipulated. The appendix has screenshots of the tables, reports, forms and queries that have been created up till now.
3.2 Hardware Interfaces
The MS Access has been used due to ease of use. The interfaces are connected and allow users to easily input and manipulate data accordingly.
The software can be used on any PC or laptop or computer device that adheres to the system requirements mentioned earlier.
3.3 Software Interfaces
MS Access is an inclusive database, and the proposed software does not require any external plugins from any other software. MS Access allows importing data tables from MS Excel, for which no external protocols or plugins are required, as the current data is on Excel sheets, it can be easily imported to the MS Access interface. MS Access will also allow user to email queries, forms, and tables to other uses using MS Outlook, but again, not external protocols are required to regulate this action, MS Access is inclusive of this.
3.4 Communications Interfaces
Microsoft Access lets user send emails using VBA module code or a macro with the DoCmd.SendObject method. This will allow user to email and share the queries, tables, and forms through the MS Outlook application, using Mail Applications Programming Interface (MAPI) to broadcast the email. This, however, can be an issue because Windows security intercepts each MAPI message and prompts the user for confirmation.
4. System Features
4.1 Create Tables
4.1.1 Description and Priority
This is a high priority task.
This will allow users to create appropriate and required tables to be used to further work on and create forms and relationships.
4.1.2 Stimulus/Response Sequences
Once user clicks create new table, a window will open which will show a blank table, which the user can fill with appropriate fields and name the table and save it. Once the table is saved, the program will inform user of successful creation. A suitable primary key need to be set for each table.
4.1.3 Functional Requirements
REQ-1: Valid field names
REQ-2: Define valid field types
REQ-3: Save table using appropriate naming conventions
4.2 Input data into tables
4.2.1 Description and Priority
This is also a high priority feature as nothing can be done without input of required data. Data will be inserted into tables through forms or the input method on the tables themselves.
4.2.2 Stimulus/ Response Sequences
Once data is entered into form/table and it is of appropriate format, it is accepted and saved.
If format or data type of data is wrong then system prompts user of the error in data type and invalidates data, asking the user to input correct data type.
4.2.3 Functional Requirements
REQ-1: Valid data type
REQ-2: Valid data length
4.3 Create Forms
4.3.1 Description and Priority
This is also a high priority feature as forms are required to provide user with interface to input data.
4.3.2 Stimulus/ Response Sequences
Once data is entered into form and it is of appropriate format, it is accepted and saved.
If format or data type of data is wrong then system prompts user of the error in data type and invalidates data, asking the user to input correct data type.
4.3.3 Functional Requirements
REQ-1: Valid data type
REQ-2: Valid data length
REQ-3: All required fields are filled
4.4 Form relationships
4.4.1 Description and Priority
This is also a high priority feature as this allows data manipulation and creation of queries which in turn will be used to create reports and other data representation.
4.4.2 Stimulus/ Response Sequences
Selecting the appropriate tables and selecting the required fields to create relationships between the tables. If primary key for a table is not defined then the relationship will not be successfully formed and will prompt user to do define primary key.
4.4.3 Functional Requirements
REQ-1: Definition of primary key
REQ-2: Availability of associated data types
4.5 Create Queries
4.5.1 Description and Priority
This is also a high priority feature as it allows the creation of reports.
4.5.2 Stimulus/ Response Sequences
Data tables will be selected for appropriate links and required sorting.
4.5.3 Functional Requirements
REQ-1: Valid data tables
REQ-2: Appropriate linking primary keys
4.6 Generate Reports
4.6.1 Description and Priority
This is also a mid-priority feature.
Allows creating of report using queries.
4.6.2 Stimulus/ Response Sequences
Appropriate query will be selected and the report will be generated based on it.
4.6.3 Functional Requirements
REQ-1: Valid query
REQ-2: Valid data present in tables
5. Other Nonfunctional Requirements
5.1 Safety Requirements
A regular backup of the data should be taken in order to ensure that in case there’s a loss of data or data gets effected due to any reason; a usable backup is available.
MS Access provides an improved security model that helps to simplify the processes of applying security to a database and of opening a database that has security enabled.
Encryption technology should be used when sharing information through the system.
5.2 Security Requirements
MS Access 2010’s new encryption technology offers new encryption technology that is stronger than the technology offered in the 2007 version, thus, an upgrade of the system software should be regularly done to ensure stricter security policies.
MS Access also allows support for third party encryption products. It allows using a third-party encryption technology if preferred.
MS Access similarly allows locking roles. The software should only fully access by authorized users given that data is important and can be misused.
Passwords should be regularly changed.
5.3 Software Quality Attributes
The system is:
- Easy to use and learn
- Easy to be transferred from one system to another
- Does not require extensive hardware or software support
- Can be managed by and run by anyone with basic know-how of MS Access
- It is adaptable to be used and run on any computer system that supports MS Access
- It is easily to maintain as MS Office offers regular security and software updates on its own.
- The software is easily reusable and extendable to other software.
- The software can be easily tested for any issues and these issues can also as easily be fixed.
Appendix A: Analysis Models
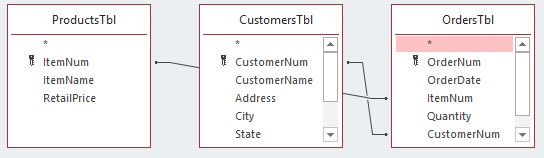
- Overall view of System
- DFD
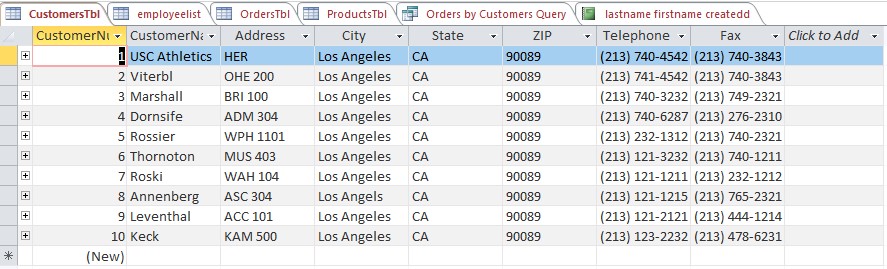
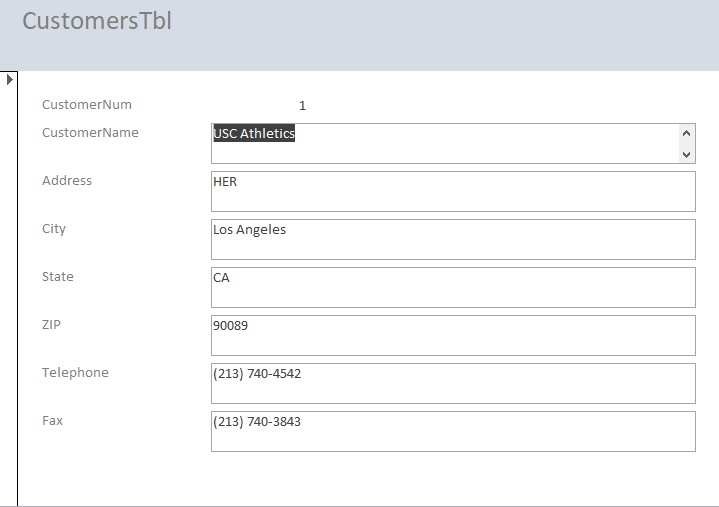
- Customer’s Table
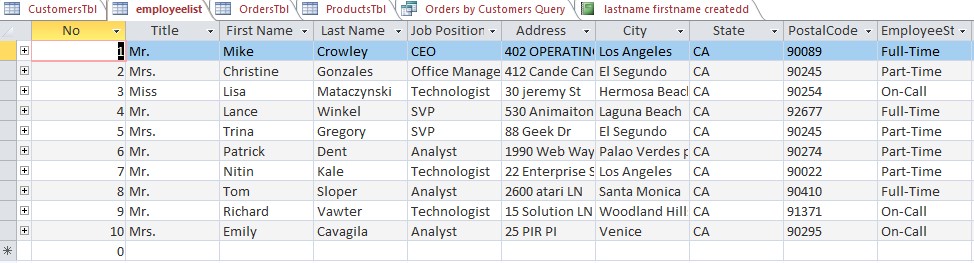
- Employee list
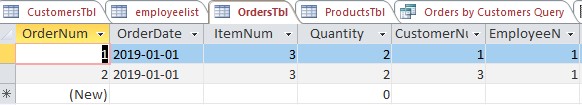
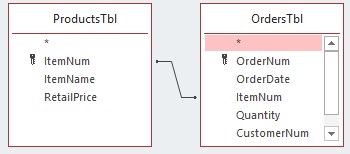
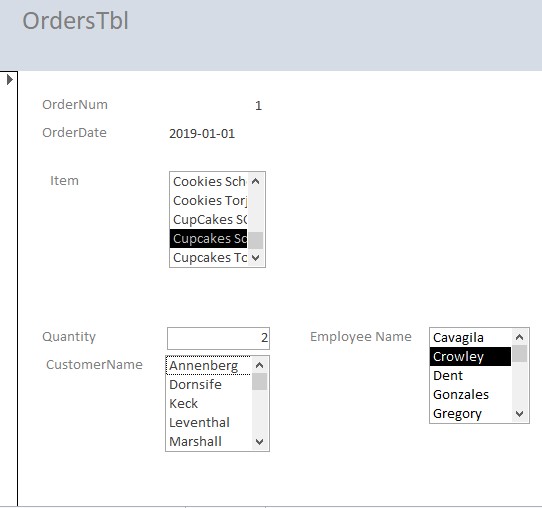
- Order’s Table
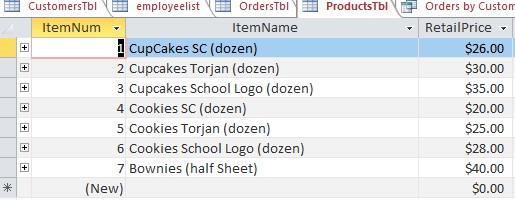
- Product’s Table
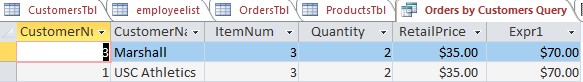
- Orders by Customers Query
- Orders for March Query
- Customers Form
- Orders Form
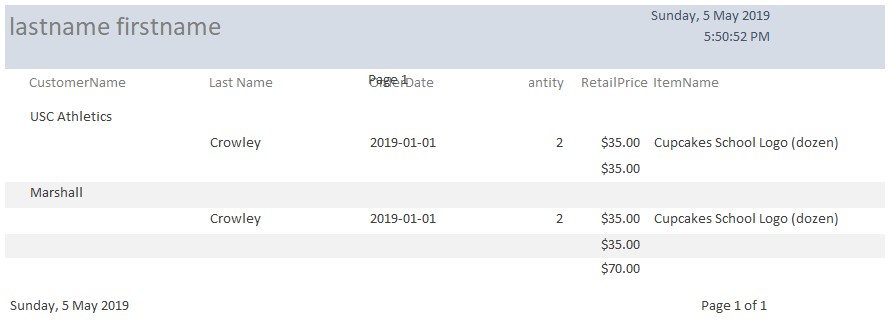
- Report (lastname, firstname)