Cryptography Part 2 Cryptographic Algorithms
{`
Kelly School of Business
Indiana University
Information Systems Graduate Programs
`}
Symmetric Algorithms
Symmetric Ciphers
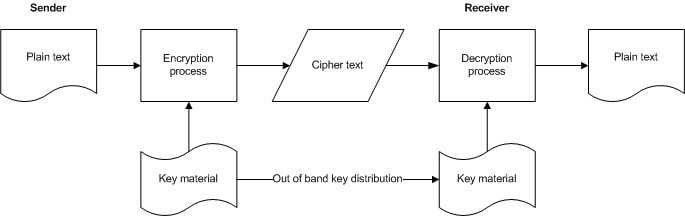
- Symmetric ciphers operate with a single (shared) key for both encryption and decryption
- Key management is a major issue – secure distribution of the key is paramount to making the cryptographic system secure
- Key must be transmitted out of band (ie using another channel)
- Advantages: very fast, secure, cheap
- Disadvantages: Does not provide for non repudiation, message integrity and access control
Symmetric Ciphers
Data Encryption Standard (DES)
- Based on the work of Harst Feistal
- Takes input block of plaintext and divides in half
- Each half is used several times with an XOR operation to alter the other half
- DES became a standard in 1977 for non-classified information
- Used extensively today (e.g. VPN)
- Susceptible to many attacks
- AES was selected as the successor by NIST in 2001
Advanced Encryption Scheme (AES)
- Based on Rijndael algorithm
- Rijndael
- Can be used with block sizes of 128, 192 or 256 bits
- Key can be 128, 192 or 256 bits with a variable number of rounds based on key size
- AES is a subset of Rijndael and supports only one block size
- Considered not breakable at this time
International Data Encryption Algorithm (IDEA)
- Developed as a replacement for AES
- Uses 128 bit key and operates on 64 bit blocks
- IDEA is patented – available free for non-commercial use
Secure and Fast Encryption Routine (SAFER)
- Patent free
- 64 or 128 block variants
- A variant is used as a block cipher for Bluetooth
Blowfish
- Extremely fast and requires very little memory
- Feistal type cipher that operates on both halves
- Variable key sizes from 32 to 448 bits and uses 64 bit input and output blocks
- Unsuitable for applications where key is changed frequently
- Considered unbreakable with today’s technology
- Twofish is an adapted version of blowfish that can operate with keys of128, 192 or 256 bits on blocks of 128 bits
RC5
- Block cipher
- Developed by Ron Rivest of RSA (rsa.com now owned by EMC2)
- Key can vary from 0 to 2040 bits and number of rounds can be adjusted from 0 to 255.
- Length of input words can be 16, 32 or 64 bits
- Four different modes of operation
RC4
- Stream cipher developed by Ron Rivest (1997)
- Most widely used stream cipher
- Used in WEP and SSL/TLS
- Variable length key ranging from 8 to 2048 bits
- Period of 10100 (key does not repeat for at least that length)
- If used with a key strength of 128, unbreakable with today's technology
- WEP issues stem from the implementation, not RC4
Advantages and Disadvantages of Symmetric Encryption Algorithms
- Advantages: Very fast, provides confidentiality along with some integrity and authentication. Can be implemented in either hardware or software
- Disadvantages
- Key management
- For n users, we need n(n-1)/2 keys
- Cannot provide non-repudiation of origin (sender and receiver have same key), access control or digital signatures
Asymmetric Algorithms
Asymmetric Algorithms
- Uses two mathematically linked but mutually exclusive keys – one for encryption and one for decryption
- Key generation
- Generate a key pair
- One half of the key pair is kept secret (private key) and the other half is given freely (public key) to anyone who wishes to communicate securely with the holder of the first half
- Asymmetric algorithms are one-way functions: the process to go from public key to the private key is mathematically infeasible
Confidential Messages
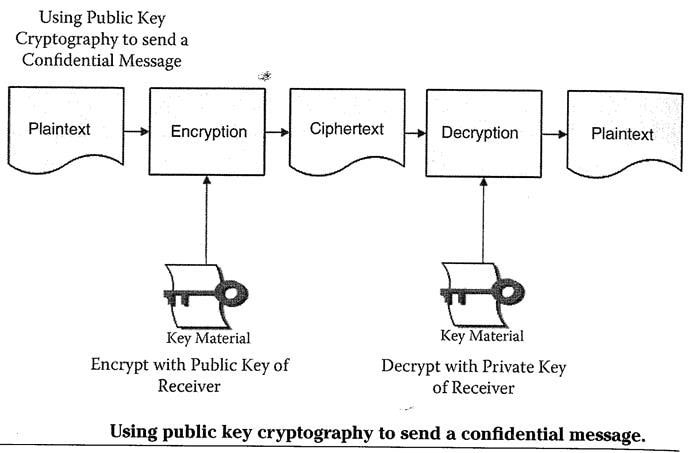
Open Message/Proof of Origin
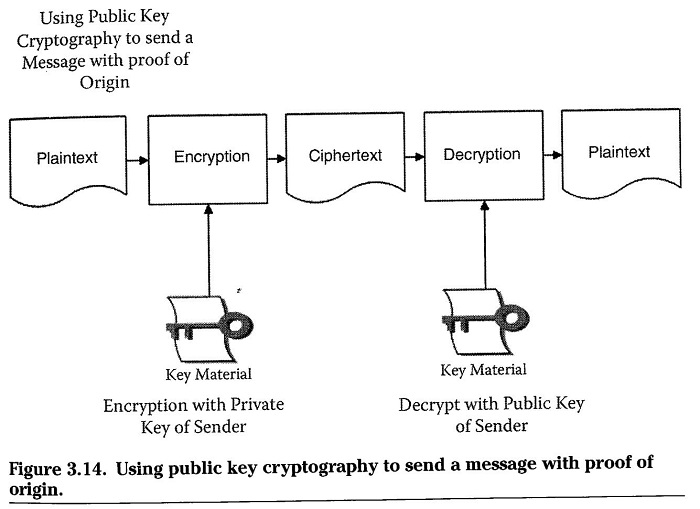
- Sender encrypts message with private key
- Receiver decrypts with sender’s public key
- Provides nonrepudiation of origin
Confidential Message with Proof of Origin
RSA
Photo from MIT Lab for CS Brochure
- RSA was developed by Ron Rivest, Adi Shamir and Len Adleman while at MIT
- Based on mathematical challenge of factoring the product of two large prime numbers
- The RSA algorithm uses large prime numbers that when multiples together are incredibly difficult to factor
- Current computational power can factor 768 bits, but factoring 1024 bits is not yet possible
- Attacking RSA
- Brute force; mathematical attacks and timing attacks
Diffie-Hellman Algorithm
- Diffie-Hellman Algorithm is a key exchange algorithm
- Used to enable two users to exchange or negotiate a secret symmetric key that can be used for message encryption
- Does not provide for message confidentiality
- Based on discrete logarithms
Key Exchange Using Diffie-Hellman
- A and B exchange public keys they calculate based on a random secret key
- Then they compute a common session key based on a formula
- The session key is then used to encrypt the data
El Gamal
- The El Gamal algorithm is based on the Diffie-Hellman Algorithm but it also includes the ability to provide message confidentiality and digital signature services along with session key exchange
Elliptical Curve Cryptography
- Based on the complex mathematics of elliptical curves
- Fast and strong
- Highest strength per key bit of any asymmetric algorithm
- Thus we can use smaller keys
- Provides confidentiality, digital signatures and message authentication
Advantages and Disadvantages of Asymmetric Key Algorithms
- Allows the transmission of confidential messages without having to worry about key transfer/key exchange
- Allows for access control and nonrepudiation of origin and delivery
- Asymmetric key encryption is extremely slow compared to symmetric key encryption
- Needs much larger keys and much more complex computation Creates much larger cipher text
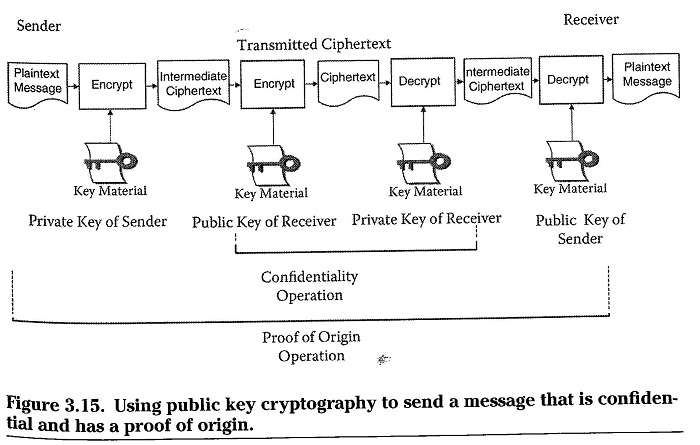
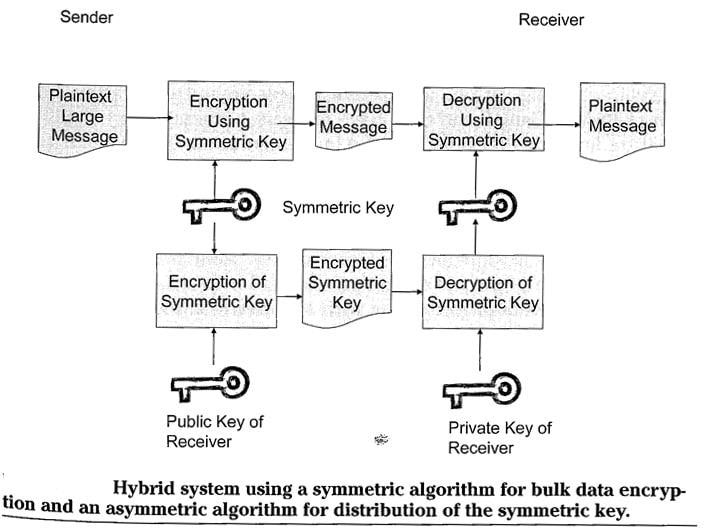
Hybrid Cryptography
- Combines the strengths of symmetric and asymmetric cryptography
- Symmetric key encryption is best for encrypting large files due to lesser computational requirement
- Asymmetric key encryption can be used to setup the initial communication session through the exchange and negotiation of symmetric keys
- In this case, the symmetric key is used only for the length of the communication and is discarded afterwards. So, it is called a session key
Hybrid System
Quantum Cryptography
Foundations of Quantum Cryptography
- Quantum cryptography is a set of protocols, systems, and procedures by which it is possible to create and distribute secret keys using the states of quantum particles like photons
- Within the laws of quantum physics, once a photon has been observed, its state is changed. Any eavesdropper trying to intercept the key automatically reveals their presence by destroying the quantum states
- Also called as quantum key distribution (QKD)
Quantum cryptography vs. traditional cryptography
- Traditional cryptography uses mathematical techniques and equations, while quantum cryptography uses principles of quantum physics
- Based on Heisenberg’s Uncertainty Principle - a particle’s position and momentum both cannot be known with unlimited accuracy at the same time
- Quantum cryptography is used to generate and distribute secret keys, which can then be used together with traditional crypto algorithms and protocols to encrypt and transfer data
- It is important to note that quantum cryptography is NOT used to encrypt data, transfer encrypted data, or store encrypted data
Basic overview of the use of quantum cryptography
- Two remote parties need to exchange data electronically in a highly secure manner
- They choose standard crypto algorithms, protocols, systems, and transport technologies to exchange the data in an encrypted form
- They use a quantum cryptography channel to generate and exchange the secret keys needed by the algorithms
- They use the secret keys generated with quantum cryptography and the classical algorithms to encrypt the data
- They exchange the encrypted data using the chosen classical protocols and transfer technologies.
Summary


